Every secure digital interaction starts with a question. How do you prove that a device is genuinely what it claims to be?
Passwords can be copied and software IDs can be cloned. Even digital certificates can be transferred from one machine to another. This problem shows up everywhere, from secure email and online transactions to software licensing and enterprise systems that need to authenticate devices, not just users.
US7493497B1 addressed this gap by moving identity down to the hardware level. It describes a digital identity device where a unique microprocessor identity is permanently etched into the chip and cryptographically bound to personal or corporate identity data. The identity cannot be separated from the physical device.
This concept sits at the center of multiple legal disputes, including cases filed by UniQom LLC against Acer, ASUSTeK Computer, Beckhoff Automation, and Micro-Star International.
To understand how this idea evolved, we used the Global Patent Search tool to trace earlier technologies that shaped hardware-bound digital identity systems.
How This Digital Identity Device Actually Works
Imagine a company issuing laptops to employees. Each laptop runs licensed software, accesses internal systems, and signs secure transactions. The challenge is not knowing who the employee is. The harder part is knowing which physical device is being used every single time.
This patent approaches that by giving the device itself a built-in identity.
At the heart of the system is a microprocessor with a unique identity etched into it during manufacturing. This identity is not generated later by software. It is physically written into the chip and cannot be changed or duplicated. You can think of it like a serial number burned into the hardware, not printed on a sticker.
That hardware identity is then used as the foundation for everything else. Personal or corporate information is stored in secure memory and encrypted using the chip’s identity as part of the encryption process. If someone removes the memory or copies the data, it becomes useless on another device because the original chip is missing.
The device can live in many forms. It might be a USB-style token, a smart card, or an internal computer component. When connected to a system, it can authenticate itself, unlock licensed software, encrypt documents, or approve secure transactions. The key idea is simple. Trust is no longer based on something the device knows, but on what the device physically is.
Key Features of the Digital Identity Device
At its core, this invention focuses on making digital identity harder to copy and easier to trust by anchoring it to physical hardware.
- Hardware-etched device identity: Each microprocessor carries a unique identity permanently etched during manufacturing, making it extremely difficult to clone or alter.
- Cryptographic binding of identity data: Personal or corporate information is encrypted using the device’s own hardware identity, ensuring the data only works with that specific chip.
- Secure storage for sensitive information: Identity details such as names, credentials, or biometric data are stored in non-volatile memory designed to remain secure even when power is removed.
- Support for multiple form factors: The identity device can be implemented as a smart card, USB device, or embedded computer component, allowing flexibility across systems.
- Built-in support for authentication and licensing: The same hardware identity can be used for secure communication, document protection, and software licensing without relying on external identifiers.
Together, these features shift digital trust away from easily copied software identifiers and toward hardware-backed identity that remains consistent across systems and use cases.
A complementary approach to enforcing trust appears in US7203844B1, which uses layered, recursive encryption to protect digital content and its own decryption logic.
Earlier Patents That Shaped Hardware-Based Digital Identity
US7493497B1 builds on ideas that were explored long before digital identity moved into hardware. Engineers had been experimenting with ways to uniquely identify devices, protect sensitive data, and control access without relying only on software.
Using the Global Patent Search tool, we looked back at earlier patents that addressed these problems from different angles. The following patents highlight key steps that led to hardware-bound digital identity systems like the one described here.
Let’s explore each one by one.
1. EP0302710A2
This IBM patent, filed in 1988, goes back to a time when software was freely copied on diskettes, often with no reliable way to control where it was used. The core problem was simple. Once software left the vendor’s hands, it could be installed and run on almost any machine.
EP0302710A2 tackled this by linking software permission directly to the computer’s CPU. Each computer carries a unique CPU identification stored in read-only memory. When software is installed for the first time, that CPU identity is combined with a source identifier from the diskette and encrypted to create a check value. That check value is stored and verified every time the software is run or copied.
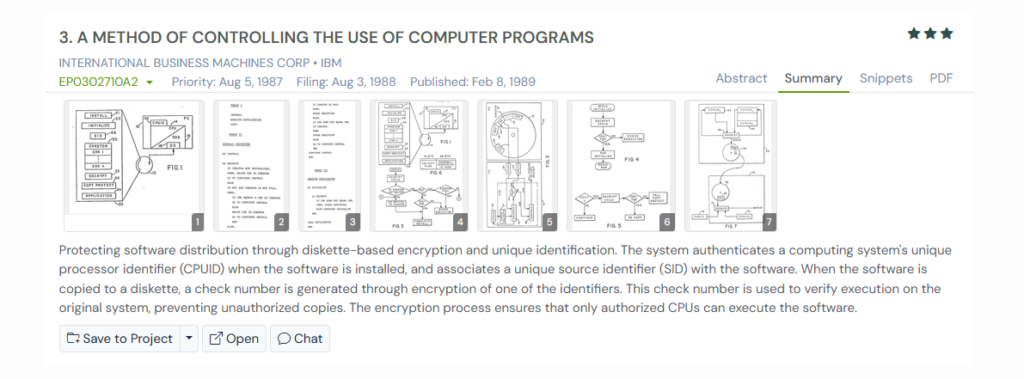
If the software is moved to a different machine, the check no longer matches and execution is blocked. This idea connects closely to US7493497B1. While IBM’s approach focuses on software control, it introduces an early version of hardware-tied identity. It shows how physical device identifiers can enforce trust.
Why It Mattered
This patent helped shift trust from software alone to the physical machine running it. By tying permission to a unique CPU identity, it showed how hardware could enforce control where software checks often failed.
US7249262B2 is worth reading if you want to understand how early systems moved beyond usernames and passwords to verify trusted devices. It offers a clear look at machine-based access control and why tying data access to specific client systems became a critical security idea.
2. CA1213069A
CA1213069A, filed in 1984 by Burroughs, looks at software protection from a different angle. Instead of relying on external checks, it embeds cryptography directly into the microprocessor itself.
Each chip carries a public encryption key that anyone can read, but the corresponding private decryption key is permanently built into the hardware and cannot be extracted.
Software vendors, including third parties, encrypt programs using the public key of a specific microprocessor. Once delivered, the program can only be decrypted and executed by that exact chip. Even if the encrypted software is intercepted or copied, it remains unusable elsewhere because the private key never leaves the processor.
This approach connects closely to US7493497B1. As both rely on binding software and identity to physical hardware so trust and control cannot be separated from the device.
Why It Mattered
This patent showed how cryptographic trust could live inside hardware, not just in software. By embedding private keys into chips, it helped shape later ideas around hardware-rooted security and device-specific identity.
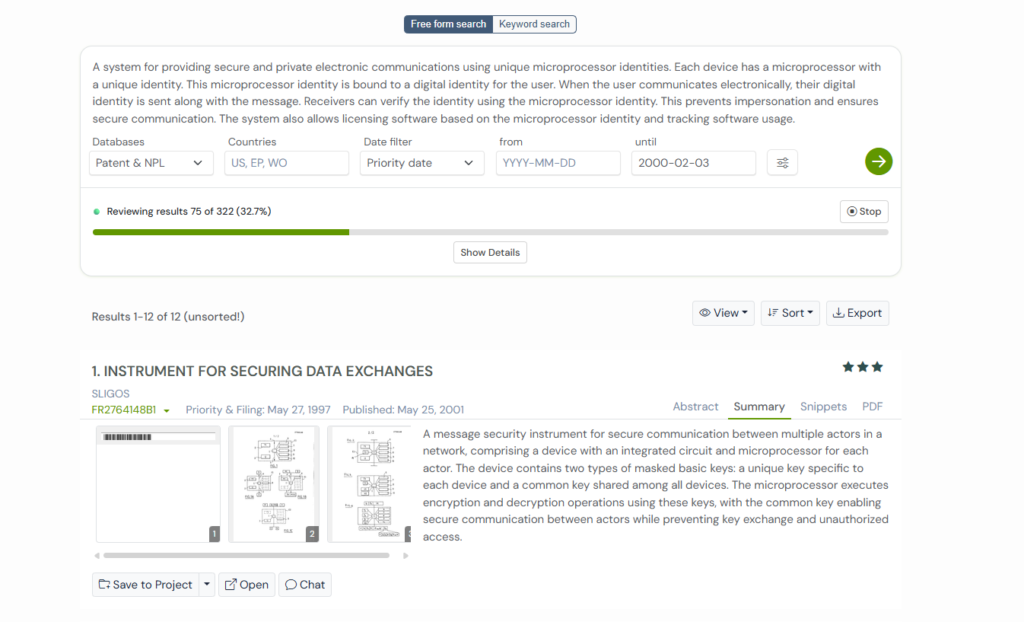
3. FR2764148B1
Filed by SLIGOS in the late 1990s, FR2764148B1 approaches secure communication through a physical device rather than through exposed software keys. The invention centers on an integrated circuit card that combines a microprocessor with protected memory areas holding cryptographic values.
Instead of giving users access to secret keys, the card performs all sensitive operations internally. Messages are sealed using hidden keys stored inside the microprocessor, and receivers verify those seals by triggering a built-in decryption function.
The device simply returns a validation or rejection result without ever revealing the keys involved.
Some versions of the system also allow the card to embed a hardware-backed identifier into the message, making it possible to confirm who sent it without exposing the underlying secrets. This hardware-controlled flow closely aligns with US7493497B1, reinforcing the shift toward device-bound identity and trust.
Why It Mattered
This patent showed how secure communication could be enforced by hardware instruments, not user-managed keys. It helped establish smart cards and secure elements as trusted carriers of identity and cryptographic control.
4. EP0175359A2
Filed by Wang Laboratories in the mid-1980s, EP0175359A2 took a practical approach to securing computer systems by controlling which physical devices are allowed to connect and operate. Instead of relying on usernames or software checks, the system uses an integrated circuit key assigned to each authorized piece of equipment.
All approved devices carry identical hardware keys. When a device attempts to connect, the system controller sends a random challenge value to both its own key and the device’s key. Each key independently generates a response, and only if the responses match does the system allow the device to function. Unauthorized equipment, lacking the correct key, is immediately rejected.
This approach aligns closely with US7493497B1 by emphasizing hardware-based trust. While Wang’s system focuses on access control rather than identity storage, it reinforces the idea that physical devices can serve as reliable gatekeepers in secure computing environments.
Why It Mattered
This patent demonstrated how hardware tokens could enforce system security without exposing secrets to users. It helped lay the foundation for later hardware-anchored authentication and trusted device models.
US9450956B1 is worth exploring if you’re interested in how devices began responding to presence rather than explicit commands. It captures an early shift toward proximity-driven trust, where identity, access, and automation happen the moment a trusted device enters the space.
5. US7197144B1
Filed by Ethos Technologies in the early 2000s, US7197144B1 takes a different approach to stopping unauthorized software use. Rather than locking a license to a single key or file, it focuses on recognizing the computer itself through a collection of hardware signals.
The system gathers multiple machine parameters and evaluates them together before granting access. By requiring a quorum of matching signals, it allows for small changes in hardware while still blocking cloned or unregistered systems. Authentication happens before the software is even delivered, reducing the risk of misuse.
This design runs quietly in the background, without user involvement. In the context of US7493497B1, it represents another step toward device-bound trust, showing how identity and permission can be tied to the system.
Why It Mattered
This patent showed how device-level authentication could be flexible yet secure. It influenced later systems that balance hardware-bound trust with usability and scalability.
US8037161B2 is a useful read for anyone working with connected devices or home networking systems. It explains a lightweight way for devices to verify trust based on real network behavior.
How These Patents Compare to US7493497B1
Looking at these five patents together makes the progression clear. Each one tackles a specific problem around trust, access, or control, but from slightly different angles.
The table below shows how each patent contributes to that evolution and how it connects back to the hardware-bound digital identity model described in US7493497B1.
| Patent | Core Focus | How It Works | Connection to US7493497B1 |
| EP0302710A2 | Software licensing control | Binds software use to a unique CPU ID stored in ROM and checks it on every run or copy | Early example of tying permission to a specific physical machine |
| CA1213069A | Hardware-embedded cryptography | Uses public encryption keys and hidden, on-chip private decryption keys | Shows how trust and execution can be locked to a specific processor |
| FR2764148B1 | Secure data exchange | Uses smart cards with hidden keys to seal and verify messages | Reinforces hardware as the trusted holder of identity and secrets |
| EP0175359A2 | System access control | Uses identical hardware keys and challenge–response checks | Demonstrates hardware-based authorization without user-managed secrets |
| US7197144B1 | Device authentication | Identifies systems using a quorum of hardware signals | Extends device-bound trust with flexibility and scalability |
How Global Patent Search Helps Connect These Ideas
When you read patents like these one by one, it is easy to miss the bigger picture. Each document focuses on a narrow technical problem; whether it be licensing software, protecting cryptographic keys, or authenticating devices.
This is where the Global Patent Search tool becomes useful. Instead of treating patents as isolated documents, GPS helps group related inventions based on underlying technical concepts.
Here’s how to use GPS effectively:
- Start with the core patent: Enter US7493497B1 to search for the concept covered and see closely related patents and NPL pop up.
- Sort results by relevance: Use the relevance option to surface patents that share technical themes like hardware identity, cryptographic binding, or device authentication.
- Scan summaries before full documents: Read short descriptions to understand what each patent is trying to solve before opening long specifications.
- Follow older references: Move backward in time to see how earlier patents contributed individual pieces of the overall system.
If you want a faster way to understand how digital identity systems developed across decades, the Global Patent Search tool helps turn scattered patents into a connected technical story. Try the tool today!
Frequently Asked Questions
1. Why is hardware-based digital identity considered more secure than software-based identity?
Hardware-based digital identity ties trust to a physical component rather than data stored in software. Software identifiers can often be copied, modified, or transferred between machines. Hardware identities are etched or embedded into devices and are far harder to duplicate, making impersonation, cloning, and unauthorized reuse significantly more difficult.
2. How does binding identity to a device help prevent software piracy?
When identity is bound to a specific device, software can be configured to run only on authorized hardware. Even if the software files are copied, they fail to execute elsewhere because the required hardware identity is missing. This shifts enforcement from licenses and keys to physical device verification.
3. What role does cryptography play in hardware-backed identity systems?
Cryptography ensures that identity data, permissions, and communications remain protected even if intercepted. In hardware-backed systems, cryptographic keys are stored or generated inside secure components and never exposed directly. This allows encryption, decryption, and authentication to happen internally without revealing sensitive information.
4. Where are hardware-bound identity systems commonly used today?
These systems appear in secure enterprise devices, smart cards, trusted platform modules, payment systems, and controlled software environments. They are especially valuable where device authenticity matters, such as regulated industries, enterprise licensing, secure communications, and systems that must reliably distinguish trusted hardware from untrusted devices.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.