Some patents solve problems you didn’t even know you had, until the technology shows up everywhere. US9450956B1 is one of those patents.
This invention, assigned to Proxense LLC, outlines a system in which applications can launch automatically when a personal device, such as a key fob, comes within range. It’s not just about access. It’s about trusted, seamless interaction using secure wireless signals and even biometric profiles. From smart offices to personal security systems, the concepts here quietly shape how we think about proximity, identity, and automation.
In this article, we’ll use the Global Patent Search (GPS) platform to explore patents that align with the core ideas behind US9450956B1. We are not here to dig into legal claims. Instead, we’re mapping out similar technologies to help you see where the innovation sits. Whether you are a technologist, researcher, or IP strategist, this data-driven deep dive is built for you.
Understanding Patent US9450956B1
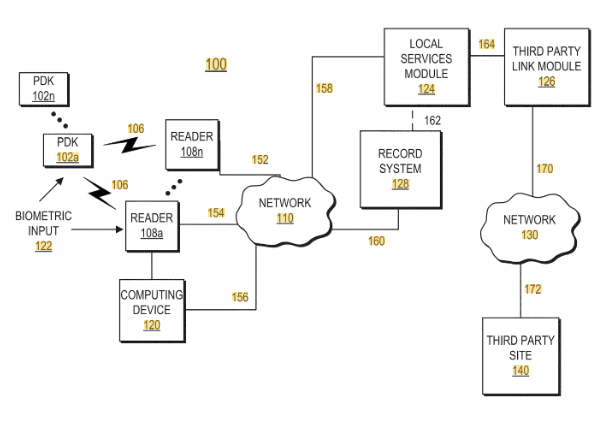
US9450956B1 describes a system that enables automatic access to applications or data through a proximity-based authentication mechanism. At the heart of this system is a device called a Personal Digital Key (PDK), a small, portable hardware unit that stores user profiles, including biometric data. Explore how similar token-based technologies appear in patents like US7177838B1.
When the PDK comes into the range of a specialized reader, it wirelessly transmits identifying information. This allows connected computing devices to automatically log the user in and launch relevant applications, eliminating the need for manual usernames and passwords.
Source: Google Patents
Its Four Key Features Are
#1. Automatic application launch via proximity detection: The system detects a PDK in range and triggers access to predefined applications.
#2. Biometric profile matching for secure authentication: Biometric data stored on the PDK is verified against a live scan to ensure identity.
#3. Auto login server integration: A backend server links user profiles with specific applications and login credentials.
#4. Priority-based access control: When multiple users are present, access is determined based on stored priority levels.
This technology is central to environments that demand secure, seamless user access, especially in sectors such as healthcare, enterprise systems, and digital identity management. The patent establishes a foundation for contactless authentication solutions utilizing personal identity tokens.
A related system with a strong focus on proximity-based authentication is US11095640B1, explored in this comparative stress test.
Similar Patents As US9450956B1
To explore the innovation landscape surrounding US9450956B1, we ran the patent through the Global Patent Search tool. Below is a quick glimpse of the GPS tool in action:
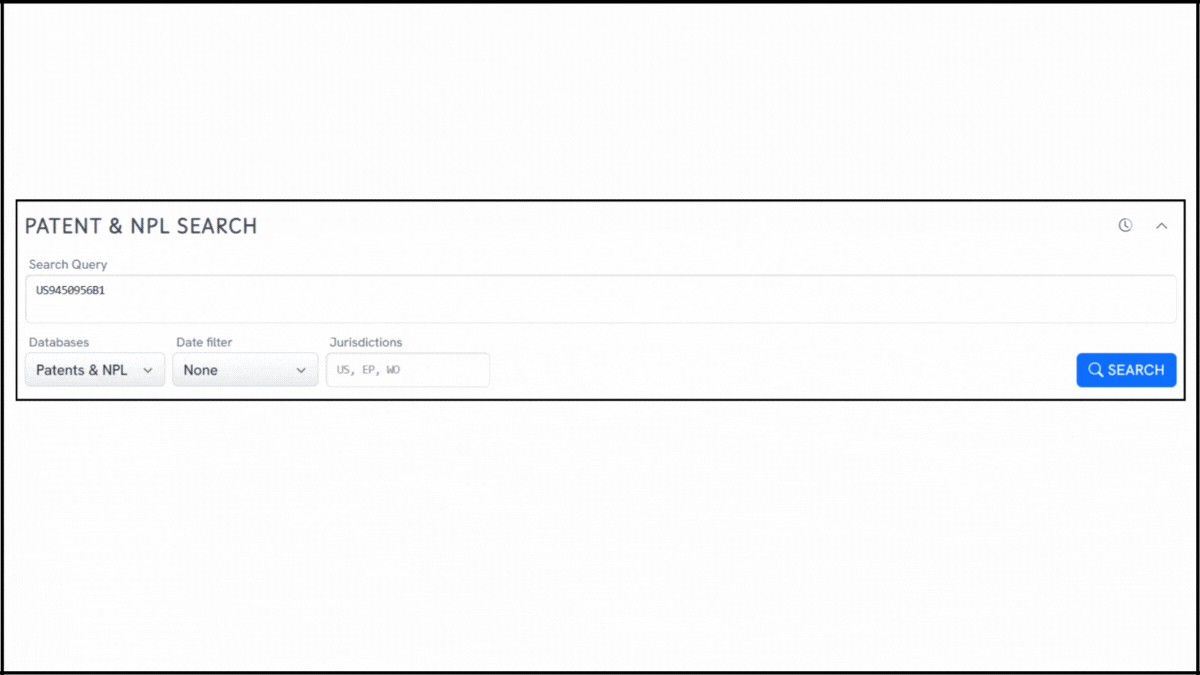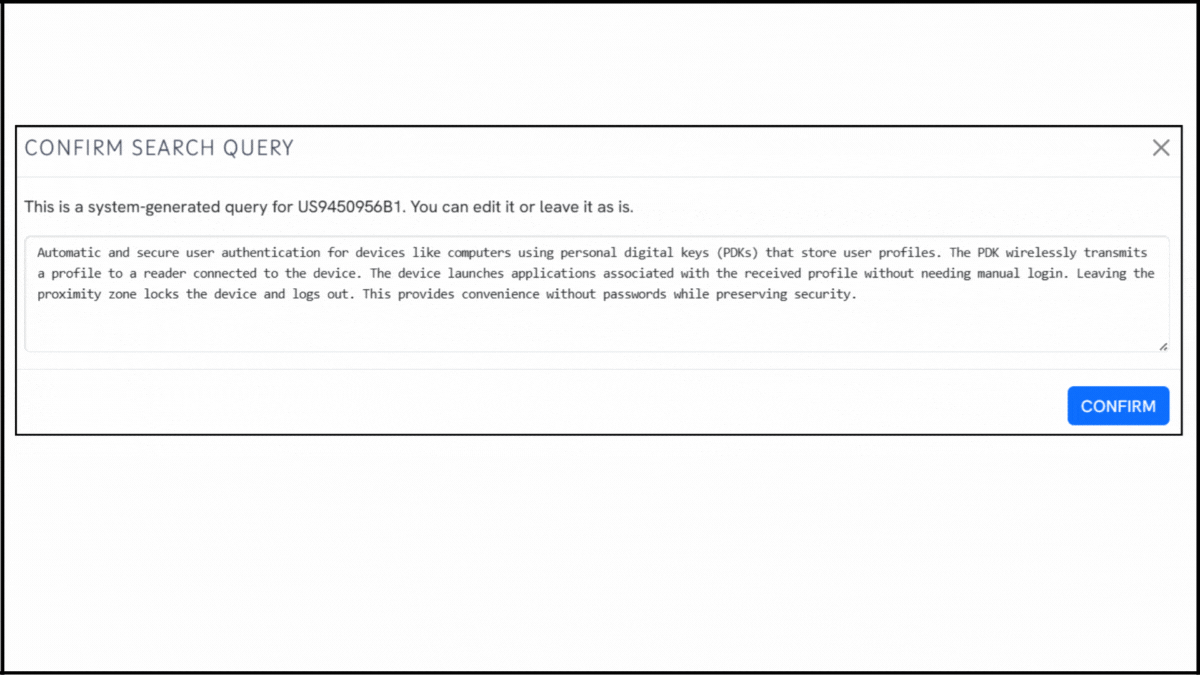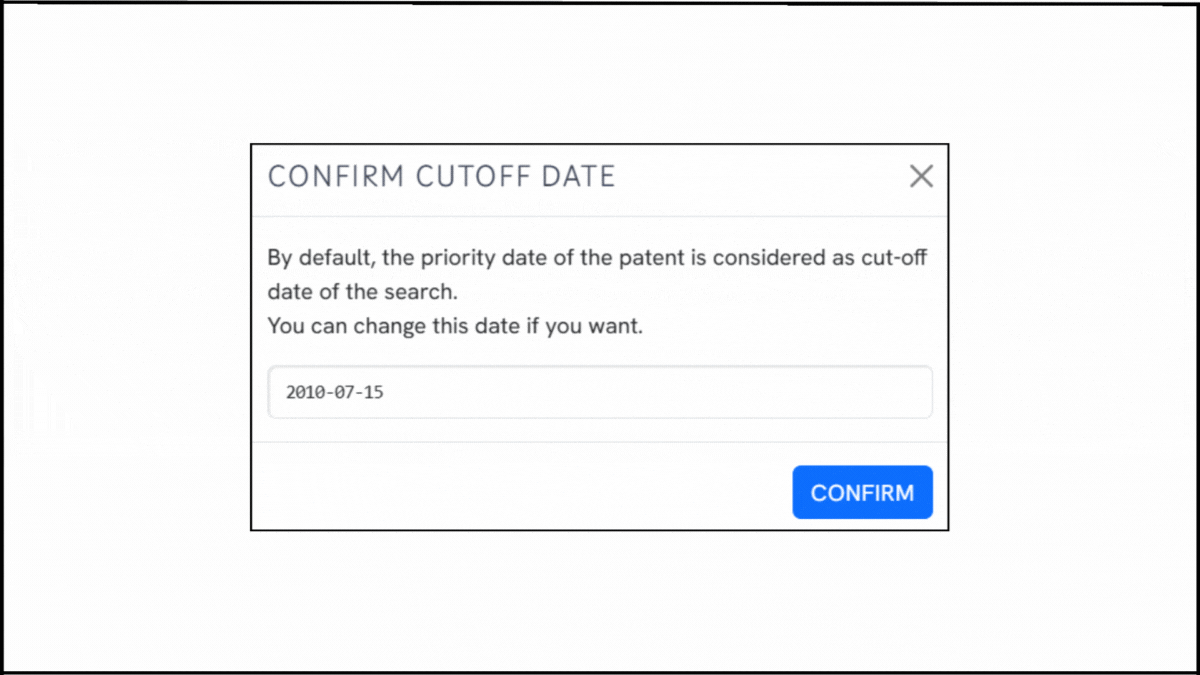
Source: Global Patent Search
This analysis surfaced a list of related patents that share conceptual similarities in proximity-based authentication, digital key management, and biometric integration. Below, we highlight five of these references that reflect comparable ideas in automated access and secure identity systems. These examples offer insight into how similar challenges have been addressed across digital access technologies.
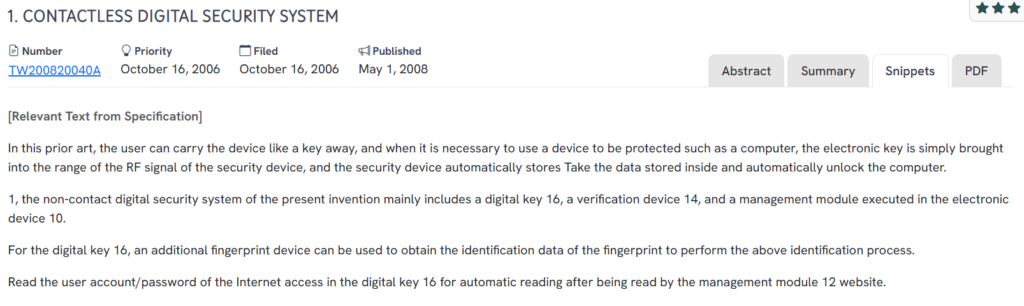
#1. TW200820040A
This Taiwanese patent, TW200820040A, published in 2008, outlines a contactless digital security system using a portable electronic key that wirelessly enables access to protected devices like computers. Simply bringing the digital key into the RF range of a verification device initiates automatic access based on stored credentials.
Below, we have added snapshots from the GPS tool highlighting the relevant snippets from the specification for the similar patents.
What This Patent Introduces To The Landscape
- Contactless authentication trigger: Access is granted when the user’s digital key comes within range of the security system, eliminating the need for physical interaction..
- Fingerprint verification option: The system optionally integrates a fingerprint module for biometric-based identity validation.
- Stored web credentials: Internet account information is stored within the key and auto-filled upon successful verification.
How It Connects To US9450956B1
- Both systems use proximity detection to initiate authentication.
- Each stores identity profiles in a portable device for access control.
- Both offer biometric integration to enhance security.
Why This Matters
TW200820040A strengthens the foundation for proximity-based authentication by integrating both secure access to devices and web credentials. It supports the broader vision behind US9450956B1: frictionless, secure user authentication without manual entry, enhanced by optional biometric safeguards.
Did you know? Personal Digital Key Patents manage presence-based access. This complements US10140514B1 Patent Audit’s time-bound images to show digital objects carrying context, profiles, and expiry rules.
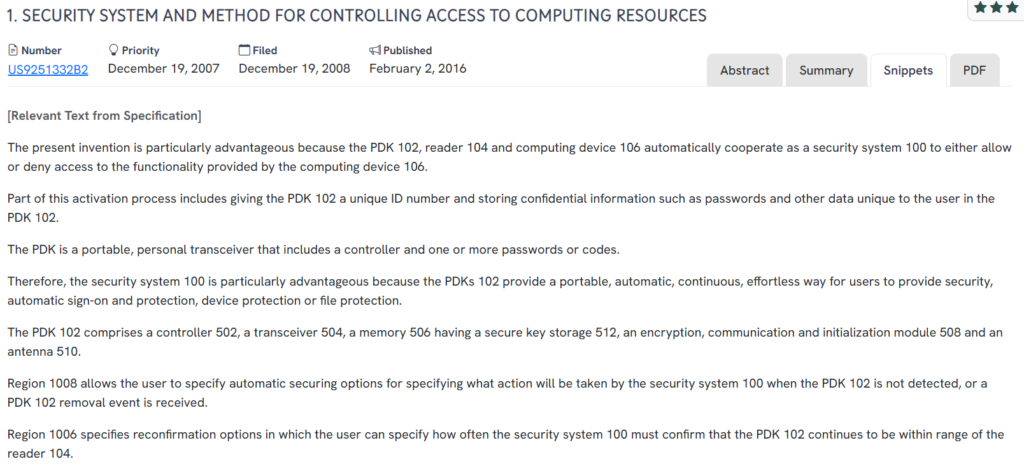
#2. US9251332B2
This US patent, US9251332B2, published in 2016, outlines a security system that uses a Personal Digital Key (PDK), reader, and computing device to form a coordinated access control framework. When the PDK is within range, it enables automatic user authentication, sign-on, and device protection, all without manual interaction.
Source: GPS
What This Patent Introduces To The Landscape
- Continuous proximity-based authentication: The system automatically detects the presence of a user’s PDK and grants or denies access based on its proximity.
- Secure key and password storage: The PDK contains a secure memory module for storing passwords, user credentials, and encryption keys.
- Fail-safe behavior upon PDK removal: The system allows custom settings to define what actions to take if the PDK goes out of range, such as locking the device or securing files.
- Biometric reconfirmation options: Users can require periodic biometric authentication via a reader or the PDK itself for added security.
- Modular encryption and initialization framework: The PDK includes specialized modules for communication security and device initialization.
How It Connects To US9450956B1
- Both rely on a Personal Digital Key that wirelessly communicates with a nearby reader to enable secure access.
- Each supports storing encrypted credentials and auto-launching applications based on profile recognition.
- Both include biometric verification mechanisms for identity confirmation.
Why This Matters
US9251332B2 further validates the concept of seamless, secure computing access using portable identity devices. Its focus on customizable locking behavior and secure key management aligns closely with the functionality of US9450956B1, helping define the modern standard for proximity-based digital security.
Recommended Read: US9251332B2 Patent Audit detailing the use of wireless PDKs for seamless login.
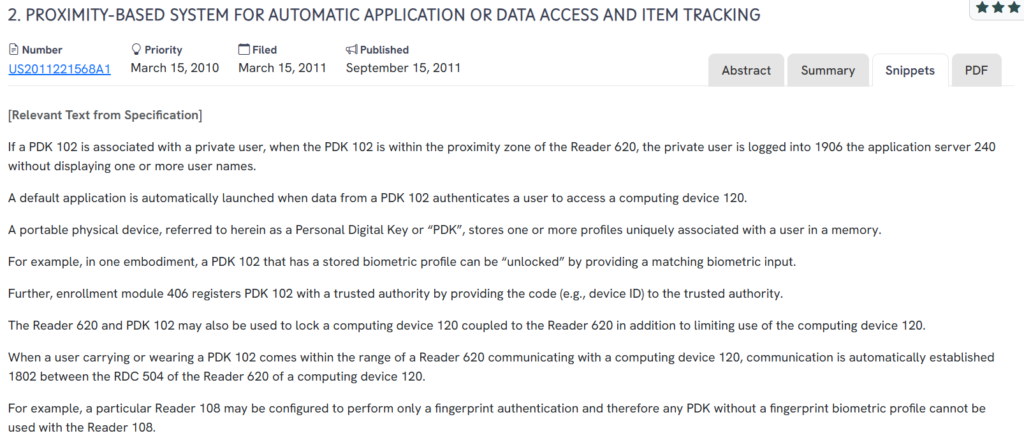
#3. US20110221568A1
This U.S. patent, US20110221568A1, published in 2011, outlines a proximity-based authentication system that utilizes a compact Personal Digital Key (PDK) to securely access applications or data. The system automatically launches applications and authenticates users based on proximity, biometric matching, and profile-based rules, without the need for usernames or passwords.
What This Patent Introduces To The Landscape
- Automatic application launch via proximity detection: When the PDK is within range of a reader, a default application is launched automatically.
- Trusted biometric profile authentication: The PDK stores biometric profiles, which must match a live scan to grant access.
- Persistent authentication windows: Users can remain authenticated for extended periods, reducing the need for repeated login.
- Secure logout and re-authentication logic: The system manages manual logout and proximity detection to control relaunch behavior.
- Application-linked profile data: The PDK transmits encrypted profile and key information that is tied to stored credentials for specific services.
How It Connects To US9450956B1
- Both rely on the PDK and reader interaction to automatically initiate authentication and application launch.
- Each supports biometric profiles stored on the PDK, used during trusted enrollment and authentication.
- Both systems eliminate the need for manual login credentials by using secure wireless communication and identity profiles.
Why This Matters
US20110221568A1 reflects a comprehensive approach to seamless, secure user access. With biometric safeguards, smart logout management, and persistent authentication windows, it closely parallels the goals of US9450956B1.
For another take on seamless secure access, check out our breakdown of US9465913B1. It reinforces the value of frictionless security systems that work silently in the background, making digital environments smarter and more user-aware.
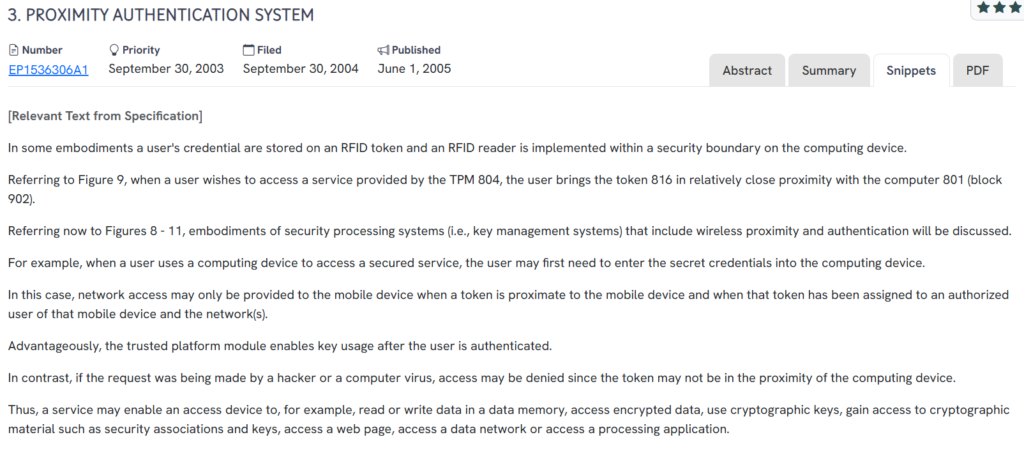
#4. EP1536306A1
This European patent, EP1536306A1, published in 2005, outlines a proximity-based authentication system that integrates RFID tokens with trusted computing environments. When a token approaches a computing device, the system authenticates the user and grants access to protected services or encrypted content, leveraging a Trusted Platform Module (TPM) for secure key handling.
What This Patent Introduces To The Landscape
- RFID-based proximity credentials: User credentials are stored on RFID tokens, which authenticate users when brought near a computing device.
- TPM integration for key management: The system uses a Trusted Platform Module to securely manage cryptographic keys and user authentication.
- Conditional network access control: Devices are only granted network access when a valid RFID token is detected nearby.
- Secure memory access: Proximity authentication allows controlled access to encrypted data, web services, and processing applications.
- In-device wireless reader placement: The RFID reader is embedded within the TPM’s secure boundary, enhancing system integrity.
How It Connects To US9450956B1
- Both systems utilize wireless, proximity-based tokens to initiate secure access.
- Each supports automatic credential-based login tied to the presence of a portable key device.
- Both enhance authentication by integrating with deeper system-level security infrastructure (TPM or auto-login servers).
Why This Matters
EP1536306A1 reinforces the role of proximity devices in trusted computing environments. By linking RFID-based credentials with TPMs, it presents a hardware-rooted solution to secure access, an idea that aligns strongly with US9450956B1’s approach to automatic, profile-driven authentication. This prior art deepens the understanding of secure, hands-free login systems.
#5. EP1814057A1
This European patent, EP1814057A1, published in 2007, outlines an authentication system where access to a personal computer or user device is permitted only when a wireless authentication transmitter is within a specific radio range. The system aims to eliminate the need for passwords while preventing unauthorized use when the user steps away from the device.
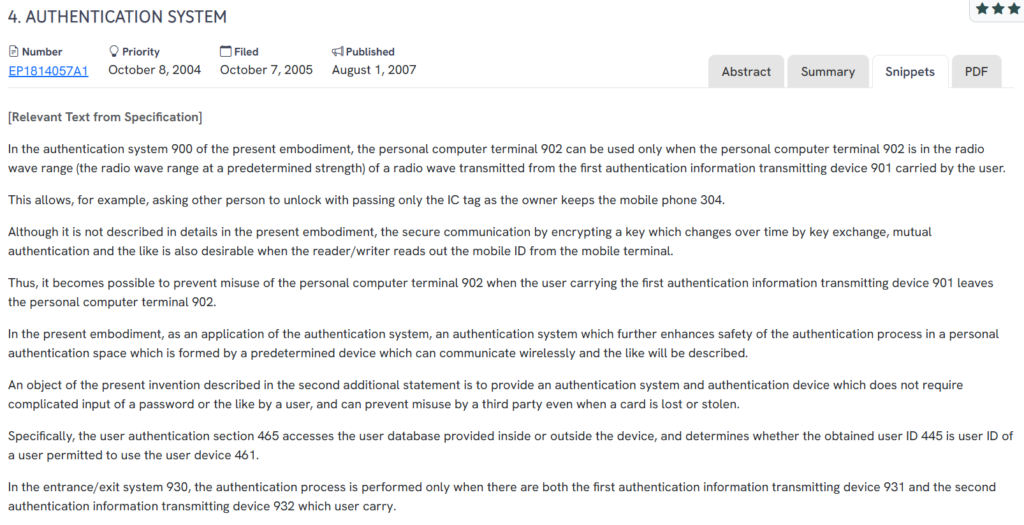
What This Patent Introduces To The Landscape
- Range-based access control: A personal computer can only be used if a paired wireless transmitter is within a predetermined signal range.
- Dual-device authentication: In some applications, two separate authentication transmitters are required for system access.
- Security against tag misuse: The system prevents unauthorized access even if the wireless transmitter (e.g., IC tag) is lost or stolen.
- Intermittent ID transmission: The authentication device sends personal ID signals periodically to reduce constant exposure.
- Encrypted key exchange: Communication between devices can include encrypted keys that change over time to prevent spoofing or interception.
How It Connects To US9450956B1
- Both systems use a wireless personal device to enable or restrict access based on proximity.
- Each avoids traditional password input by relying on automatic detection and secure profile matching.
- Both focus on preventing unauthorized use when the key device is out of range or absent.
Why This Matters
EP1814057A1 highlights an approach to user authentication that emphasizes passive, proximity-based access with added encryption safeguards. This aligns with the intent behind US9450956B1, underscoring the importance of seamless authentication systems that safeguard user data without compromising the user experience.
Did you know? Proximity-Based Authentication Patents show context-aware infrastructure responding dynamically. This echoes US11751302B2 Patent Audit’s adaptive lighting systems controlled by user input.
How To Find Related Patents Using Global Patent Search
Understanding the broader patent landscape is key when analyzing proximity-based authentication, wireless login systems, or biometric access control. The Global Patent Search tool streamlines this process, helping users identify technologies that reflect similar approaches.If you want to compare GPS with other top analysis platforms, here’s our curated guide.
1. Enter the patent number into GPS: Start by entering a patent number like US9450956B1 into the GPS tool. The platform turns it into a smart query, which you can refine using terms like biometric login, proximity device, or automatic application launch.

2. Explore conceptual snippets: Instead of a claim-by-claim feature map, GPS now provides curated text snippets. These highlight how other systems handle wireless identification, secure user authentication, or passive device recognition.
3. Identify related inventions: The tool surfaces patents that address proximity-triggered access, biometric verification, or encrypted credential storage, revealing how others have approached trusted computing and device protection.
4. Compare systems, not legal claims: Rather than relying on formal legal language, GPS focuses on system-level behavior. This allows users to trace conceptual overlap and technical architecture, even across different application areas.
5. Accelerate cross-domain insights: Whether you’re working in enterprise security, healthcare IT, or consumer electronics, GPS helps uncover similar inventions that might otherwise remain siloed.
With this approach, Global Patent Search gives innovators, analysts, and IP professionals a structured, concept-first way to explore related patents and sharpen their technology strategies.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.



