We’ve all had that moment where we open a website, and something feels off. Maybe the page glitches, loads strange pop-ups, or slows the computer down for no reason. The truth is, even normal websites can carry hidden code that our browsers aren’t always prepared to handle.
US9118712B2 outlines a method to solve this problem. It introduces a safer way to browse by putting a secure system between the user and the internet. This system collects the webpage first, cleans out anything risky inside virtual machines, and then sends only a safe, rebuilt version back to the user’s browser.
The patent is also central to a litigation by assignee Touchpoint Projection Solutions, which shows how central this idea has become in web security discussions.
Using the Global Patent Search tool, we explored how this patent fits into the bigger picture of making everyday browsing safer. But first let’s take a look at what this patent exactly covers.
Understanding the Core Idea Behind US9118712B2
To understand this patent, it helps to start with the basic problem. Our browsers do a lot more than show text and images. They execute scripts, run small programs, and load code from many different sources. That flexibility makes browsing smooth, but it also opens the door for malware to slip in without warning.
US9118712B2 tries to change how this entire process works. Instead of letting the user’s browser handle the raw website code, the patent places a secure system in the middle. This system receives the webpage first, breaks it apart in a protected environment, and rebuilds a clean version that the user can safely view.
The smart part is how it handles risky elements. Executable code is opened inside temporary virtual machines. If anything suspicious happens, those machines are destroyed instantly. Even during normal browsing, the system regularly flips between fresh virtual machines, making it harder for hidden threats to survive.
In simple terms, the patent creates a safe buffer zone so harmful website code never reaches the user’s actual device.
The Key Components That Make This System Work
US9118712B2 isn’t just about blocking bad websites. It changes the entire journey of how a webpage reaches a user. Here are the parts that make the system effective.
- A safe middle layer: Instead of sending the user’s browser directly to the website, all requests first go to a remote security system. This system handles the risky part of the process and shields the user from raw website code.
- Rendering pages into a clean format: When the security system receives data from the internet, it doesn’t pass it forward as-is. It turns the page into a fresh, safe version, like rebuilding it into an XML page with simple styling, so nothing harmful travels to the user’s device.
- Virtual machines for risky content: Any part of a webpage that looks executable or suspicious is opened inside a temporary virtual machine. If something behaves oddly, that machine is wiped immediately.
- Regular flips for added safety: The system doesn’t wait for threats to appear. It routinely switches to new virtual machines during normal browsing, which makes it hard for hidden malware to stick around.
- No extra load on the user’s computer: All the heavy processing happens remotely. The user only receives a safe, final version of the webpage, so even older or simpler devices stay secure.
These building blocks show how the patent turns normal web browsing into a much safer process, and now it helps to look at other inventions that laid the groundwork for this approach.
You can also explore how US7523497B2 tackles network-level denial-of-service risks, offering a useful contrast to the browser-focused isolation approach in US9118712B2.
How Earlier Ideas Help Us Understand This Patent Better
Before we look at what US9118712B2 enabled, it helps to step back and see what came before it. Web security didn’t suddenly shift to remote rendering and virtual machines overnight.
Different inventors tried different approaches; some focused on isolating the browser, some on filtering risky content, and others on controlling how web pages are delivered.
By comparing those earlier ideas with this patent using the GPS tool, we get a clearer picture of how the field evolved and how US9118712B2 builds on those foundations.
Let’s explore some of them.
1. US2007016949A1
Anyone who has used the internet long enough has seen how quickly a harmless webpage can turn into a doorway for trouble. A small script hidden inside a page can steal data, hijack browser settings, or quietly inject malware. Because browsers run so many types of code, attackers often find small gaps to slip through.
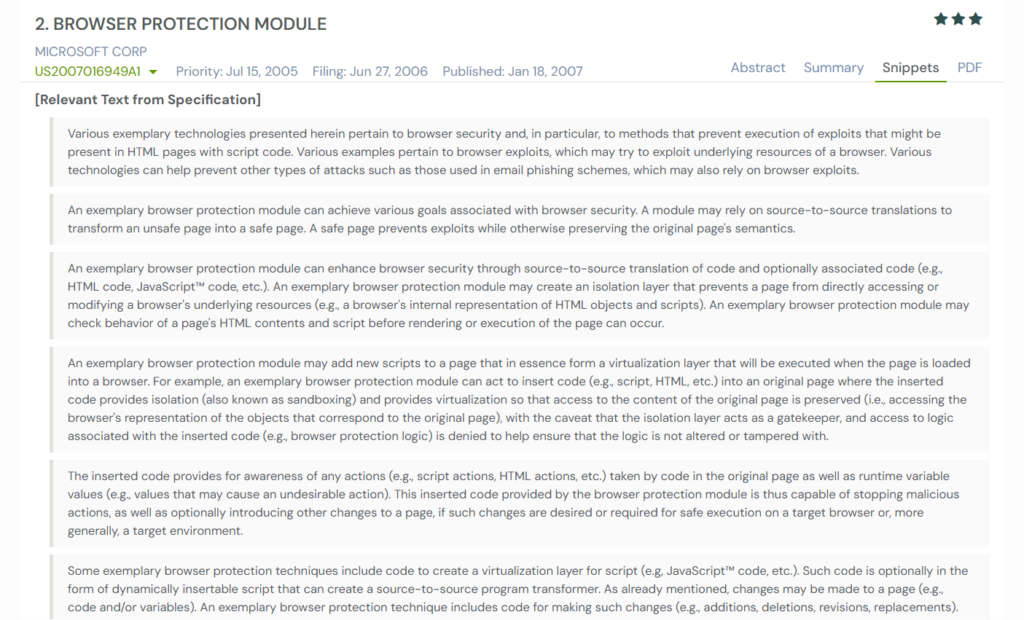
Microsoft’s US2007016949A1, filed in 2006, addresses this problem by changing what the browser actually receives.
Instead of allowing a webpage to run its own scripts freely, this invention rewrites the page first. It looks at the HTML and JavaScript, removes risky parts, inserts its own protective code, and turns the original page into a safe page that behaves the same but no longer has access to sensitive browser resources.
In simple terms, it creates an isolation layer inside the browser by transforming every page before the browser renders it.
This idea overlaps with US9118712B2 because both patents try to protect users by reworking the incoming webpage before it reaches the browser. While the Microsoft patent rewrites the code directly, US9118712B2 takes this concept further by processing the content remotely and using virtual machines to isolate dangerous elements.
Both solutions share the same goal of keeping harmful scripts away from the user’s real browsing environment.
Why this patent is important
The patent shows one of the early attempts to control browser based attacks without relying on traditional antivirus software.
By transforming unsafe code into safe code and inserting its own checks, the system helped shape a new direction in web security, where pages are cleaned and verified before the user sees them. This shift set the stage for modern isolation and remote rendering techniques that appear in patents like US9118712B2.
2. US2009070663A1
Scripts can be really unpredictable. One moment, a page is loading smoothly, and then suddenly it reveals hidden code when the browser processes a form, a pop-up, or a dynamic element. These surprises are exactly where attackers hide their tricks. Even a tiny script buried inside normal markup can cause the browser to execute something harmful.
US2009070663A1, filed by Microsoft Corporation in 2007, introduces a solution that behaves like a smart gatekeeper on the user’s device. Instead of letting the browser talk directly to the script engine, the proxy engine steps in between.
It intercepts every script call, checks what the script is trying to do, and decides whether it should run or be blocked. If the script looks safe, it forwards it to the native script engine. If it appears in a place where scripts are not allowed, or shows signs of misuse, the proxy engine cancels it before it executes. It can even watch DOM events to spot scripts that reveal themselves only after the page starts loading.
The system described in US9118712B2 does something similar remotely by rebuilding an entirely safe version of the webpage. Both aim to manage risk by inspecting content at the moment it arrives, not after it causes damage.
Why this patent is important
This patent gives a clear example of early efforts to manage scripts at a very fine-grained level. By monitoring script events, DOM changes, and script-free zones, it provides a more precise way to block harmful behavior without shutting down legitimate functionality.
These ideas help explain the shift toward layered, event based protection models that influenced later remote rendering approaches like the one in US9118712B2.
3. US2011197272A1
Sometimes a webpage loads more than what we expect. A simple click can trigger hidden scripts that try to run quietly in the background. These small pieces of code can steal information, redirect users, or attempt to take control of the browser without showing any obvious signs.
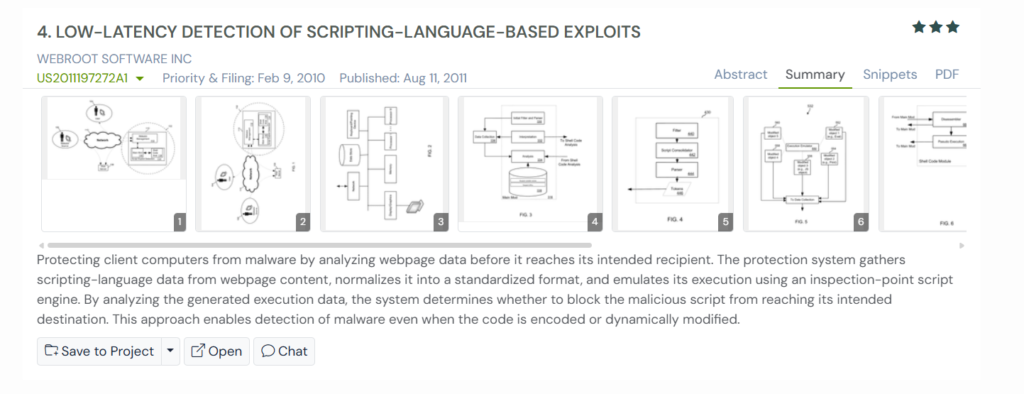
US2011197272A1, filed by Webroot Software Inc in 2010, focuses on stopping these script-based attacks before they become a problem.
The invention places a security center between the user and the website. This center receives the webpage first, extracts all scripting language content, and turns it into a normalized form that can be safely examined.
The system then emulates the script inside a controlled environment where each step is monitored. If the script behaves in a suspicious way, the content is blocked. If it behaves normally, the cleaned version is forwarded to the user.
This idea fits closely with US9118712B2 because both keep dangerous content away from the user’s device. This Webroot patent uses script emulation and inspection points to understand how a script might behave. US9118712B2 uses virtual machines to rebuild a safe version of the webpage. Both prioritize early detection so harmful content never reaches the real browsing environment.
Why this patent is important
The patent highlights how cloud-based security started to evolve. By inspecting scripts outside the user’s device and using emulation instead of direct execution, it created a safer path for handling unpredictable, script-heavy webpages.
These ideas helped shape modern isolation and remote inspection strategies that continue in later technologies, such as those described in US9118712B2.
If you’re exploring how deeper network layers influence web safety, this breakdown of US9584633B2 highlights how flattened communication paths improve secure data delivery.
4. US8464318B1
Modern web applications rely heavily on client side logic. They store session data in cookies, run long chains of JavaScript tasks, and constantly update the interface as the user interacts. This works smoothly when everything is trusted. But when users connect from unknown devices or unsecured networks, the application has no way of knowing whether the client side code has been tampered with or manipulated.
US8464318B1, filed by Hallak Renen and published in 2013, shifts this burden away from the user entirely. The invention introduces a secure gateway that executes all client side application code on behalf of the client. The gateway loads the application, processes the scripts, manages cookies, and handles all logic internally.
The user receives only the interface output they need to see, while everything risky stays inside the protected gateway environment. This keeps the user safe from malicious client side attacks and also reassures the server that the client side code has not been altered.
This approach aligns closely with US9118712B2 because both patents remove risky operations from the user’s device. Here the focus is on relocating web application execution to a secure gateway. Both reduce exposure by placing an intelligent checkpoint between the user and the actual code.
Why this patent is important
The patent marks an important shift in web security by relocating client side execution to a trusted middle layer. It protects users from harmful scripts and protects servers from tampered requests. These ideas support the broader move toward remote processing and isolated execution seen in technologies such as US9118712B2.
Real-time communication risks are covered in our US7756983B2 analysis, which explains how traffic can be secured during high-volume interactions.
5. US8356352B1
Platforms that allow users to upload their own content face a completely different challenge compared to regular browsing. The risk does not come from a webpage the user visits. It comes from the code that users themselves try to post.
A single JavaScript snippet hidden inside a profile page, blog comment, or community widget can quietly redirect traffic, steal data, or drop malware onto anyone who views it.
US8356352B1, filed in 2008 by Symantec Corp., addresses this problem by running every piece of user generated content inside a virtual machine before it goes live. The content is executed just like it would run in a real browser, but inside a contained environment where nothing can escape.
If the virtual machine sees suspicious activity, unusual script behavior, or signs of an exploit, the content is blocked automatically. If everything behaves normally, the platform allows the content to be published.
This connects naturally with US9118712B2 because both patents use isolated execution to uncover hidden malicious actions. The difference lies in the purpose. But together, they represent two sides of the same safety idea: prevent attacks by observing code in a sealed, controlled environment first.
Why this patent is important
By forcing user generated content to reveal its behavior in a virtual machine, the invention makes it much harder for attackers to hide malicious scripts behind obfuscation or clever encoding.
It protects entire communities from harmful uploads and reduces the load on intrusion detection and antivirus systems by filtering threats early, long before they ever reach a user’s browser.
Comparing US9118712B2 with the Related Patents
Before we go ahead, it helps to take a quick pause and look at all five patents together. Each one tries to solve the same problem in its own way: keeping unsafe scripts and web content away from real users. But the techniques are different. Some rewrite the page, some intercept browser events, some emulate suspicious code, and some run everything on a secure gateway.
Putting these ideas side by side makes the strengths and boundaries of each approach much easier to see. It also highlights what truly sets US9118712B2 apart, especially in the way it remotely renders entire pages into safe content.
| Patent Number | Assignee | Core Innovation | How It Connects to US9118712B2 | Impact on Web Security |
| US2007016949A1 – Browser Protection Module | Microsoft Corp | Rewrites unsafe HTML/JS into a safe version using source-to-source translation and inserts a sandbox-like virtualization layer. | Similar goal of transforming unsafe content into safe content before it reaches the browser, but does so by rewriting code instead of fully rendering it remotely. | Strengthened browser-side defenses and reduced exploit execution inside the client browser. |
| US2009070663A1 – Proxy Engine for Custom Handling of Web Content | Microsoft Corp | Intercepts script events between the browser and script engine, filtering harmful events using custom handlers. | Shares the idea of inserting a security layer between the browser and untrusted web code, but operates locally on the client device instead of remote rendering. | Improved protection against malicious script execution by tightly monitoring browser-script interactions. |
| US2011197272A1 – Low-Latency Detection of Scripting-Language-Based Exploits | Webroot Software Inc | Emulates script behavior in a virtual environment and analyzes it in real time to detect suspicious activity. | Overlaps in using virtual environments to detect threats, but US9118712B2 uses virtual machines mainly to safely render content rather than emulate suspicious scripts. | Enabled early detection of hidden or obfuscated script-based attacks through near real-time analysis. |
| US8464318B1 – System and Method for Protecting Web Clients and Web-Based Applications | Hallak Renen | Runs all client-side web application code on a secure gateway and sends only safe UI updates to the user. | Closely aligns with US9118712B2’s concept of remote execution, but focuses on executing application code, while US9118712B2 focuses on rendering full web pages into safe visual output. | Provided strong isolation by shifting all client-side logic to a trusted remote gateway. |
| US8356352B1 – Security Scanner for User-Generated Web Content | Symantec Corp | Executes user-generated content in a virtual machine to detect malicious behavior before posting it online. | Similar use of virtual machines, but applied at content submission time rather than during live browsing or page delivery. | Reduced risk for platforms hosting user-generated content by filtering out harmful scripts before publication. |
How the GPS Tool Helps You Uncover the Bigger Picture
When you study a patent like US9118712B2, it tells only one chapter of a much bigger story. Ideas in web security usually grow together, overlap, or evolve from earlier attempts to solve similar problems.
The Global Patent Search tool makes it easy to trace those connections. It shows how one invention builds on another and how different approaches shape the direction of an entire technology area.
Instead of manually digging through dozens of documents, GPS pulls everything into one clean view. You can immediately see which patents share the same concepts, how they differ, and what new angle each inventor brought in.
Here’s how you can use GPS to explore these connections effortlessly:
- Start with any patent number: Enter something like US9118712B2 or even a small description of the invention. GPS uses this as your starting point.
- Check the related results: The tool surfaces patents addressing similar problems or techniques, helping you understand the broader ecosystem.
- Open the snippets: Each related document comes with short claim or description extracts that make it easy to spot overlaps at a glance.
- Dive deeper only when needed: If a patent stands out, you can explore the full text to compare architectures, decision flows, or threat-handling methods.
- Filter by what you care about: Whether it’s browser isolation, virtual machines, script analysis, or gateway security, GPS lets you focus on the sub-topics that matter most to you by using the sort by relevance feature.
- Build a clearer understanding: By seeing how all the ideas connect, you get a more complete view of how the subject patent fits into the evolution of secure browsing.
The GPS tool turns complex patent exploration into a simple, guided journey.
It helps you see the bigger picture behind US9118712B2 and understand how its concepts grew from earlier innovations and continue shaping the future of web security.
Try the tool today to explore more such patents!
Frequently asked questions
1. Why is web browsing still risky even with antivirus software installed?
Antivirus tools mainly catch known threats. Modern attacks often hide inside scripts, web pages, or dynamic content that loads inside your browser. These threats don’t always look like traditional malware files, so they can slip past basic antivirus checks.
2. What does remote rendering mean in web security?
Remote rendering means the web page is opened and processed on a secure server first, not on your device. Your browser only receives a clean, safe version of the page. This keeps harmful scripts or hidden code away from your system entirely.
3. How do virtual machines help in detecting malicious behavior?
Virtual machines create a controlled environment where suspicious code can run safely. If the code behaves strangely or tries to attack the system, the VM absorbs the damage, keeping the real device protected.
4. What makes script-based attacks so dangerous?
Scripts like JavaScript and Flash can run automatically when a page loads. Attackers use them to steal data, hijack sessions, or download malware without the user clicking anything. Because scripts are flexible and easy to hide, they’re one of the most common attack methods on the web.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.