Technology moves fast, but some ideas remain essential no matter how much the landscape changes. US9251332B2, assigned to Proxense LLC, is one of those ideas.
This patent introduces a system that controls computer access using a personal digital key, a wireless device that confirms a user’s presence before unlocking functionality. It seamlessly integrates hardware, software, and authentication protocols to provide a comprehensive access control method. From secure login environments to presence-based computing, the core concept feels more relevant than ever in today’s security-conscious tech landscape.
In this article, we turn to the Global Patent Search (GPS) tool to explore patents with similar design approaches or related security mechanisms. This isn’t about litigation, it’s about identifying overlapping ideas, tracking innovation patterns, and revealing how access control technology has evolved.
If you’re in R&D, IP strategy, or simply tracking tech trends, this research-backed exploration is for you.
Understanding Patent US9251332B2
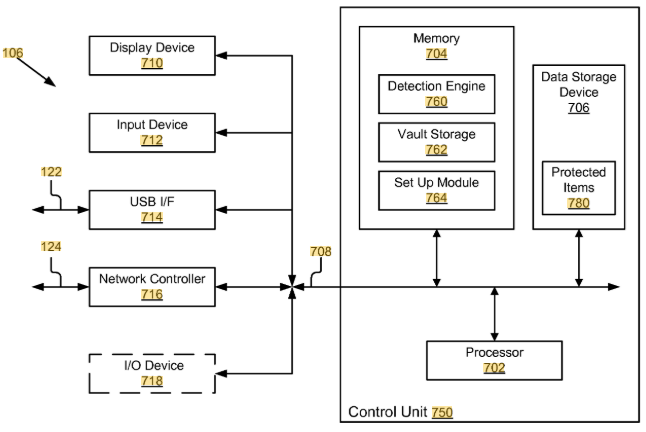
US9251332B2 describes a security system and method for controlling access to computing resources. At its core, the invention uses a wireless personal digital key (PDK), a reader, and a computing device. The PDK communicates with the reader, and based on this interaction, access to the computing system is either granted or denied, automatically and without user intervention.
Source: Google Patents
Its Four Key Features Are
#1. Wireless Personal Digital Key (PDK): A portable device that stores encrypted user credentials and communicates via radio frequency.
#2. Detection engine: Installed on the computing device, it monitors file access and determines if the PDK is present.
#3. Vault storage and setup module: Secure, encrypted storage that holds system-specific setup records used for access control.
#4. Automated access control: Access to files, applications, or third-party systems is enabled or restricted based on the proximity and status of the PDK.
The technology stands out for its seamless, proximity-based control over computing resources, requiring no user input once it is configured. It reflects a shift toward invisible security, where hardware and software work together in the background to protect sensitive data.
For another early example of secure proximity-based data access, see how US9465913B1 tackles mobile device-triggered encryption in this analysis of secure data access patents.
Did you know? Access Control Security System Patents integrate environmental awareness into security layers. This is similar to US10391344B2 and related patents that embed moisture detection into venting for greater reliability.
Similar Patents As US9251332B2
To explore the innovation landscape surrounding US9251332B2, we ran the patent through the Global Patent Search tool. Below is a quick glimpse of the GPS tool in action:
Source: Global Patent Search
This analysis surfaced a list of related patents that share conceptual and structural similarities in wireless access control and intelligent key-based security. Below, we highlight five of these references that reflect comparable approaches to device authentication and encrypted access. These examples demonstrate how related challenges in digital security have been addressed through the use of physical key systems and encrypted communications.
#1. CN101009555A
This Chinese patent, CN101009555A, published in 2007, introduces an intelligent key device system that combines online and wireless components to authenticate user access. It also enables encrypted communication with a host computer, supporting secure data transfer, digital signatures, and tamper-proof key storage.
Below, we have added snapshots from the GPS tool highlighting the relevant snippets from the specification for the similar patents.

What This Patent Introduces To The Landscape
- Dual-mode secure access system: Combines a physical online device with a wireless interface for safe interaction with the host.
- Support for PKI and digital signatures: Enables strong cryptographic functions, including encryption and SSL-based safenet communication.
- Tamper-resistant hardware architecture: Ensures the private key remains inaccessible even if physical access to the device is obtained.
- User-centric security workflow: Addresses usability issues tied to forgotten or lost authentication tools.
How it connects to US9251332B2?
- Both patents feature proximity-based control through a wireless personal device.
- They use hardware-stored credentials to authenticate user access without manual entry.
- Each focuses on securing digital resources through background communication with an external security device.
Why This Matters
This reference reinforces the viability of physical key systems in secure computing environments. It parallels US9251332B2 in designing frictionless, proximity-triggered authentication, pointing to a broader trend of integrating hardware-level encryption into everyday access control.
A similar debate around identity-driven access control is unfolding in DatRec LLC’s litigation involving US8381309B2. The patent outlines how verified identities shape communication permissions across a network, making it highly relevant when evaluating secure access technologies.
#2. DE202004021130U1
This German utility model, DE202004021130U1, published in 2006, describes a user authentication system, often applied in environments like hospitals, where a transponder-based device activates a secure communication channel between an access point and designated resources, such as a hard drive.
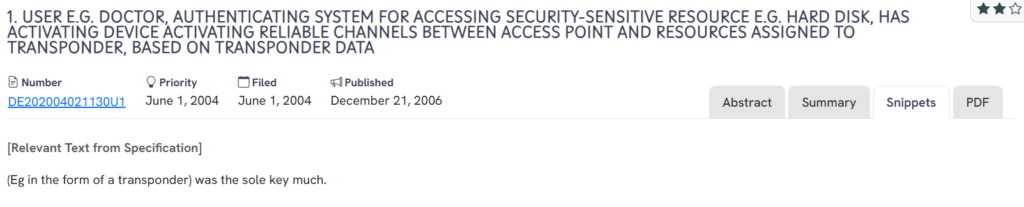
What This Patent Introduces To The Landscape
- Transponder-based access control: Utilizes a wireless transponder (e.g., RFID) as the core authentication mechanism.
- Reliable channel activation: Establishes secure communication channels dynamically between the user’s device and protected resources.
- Contextual use in high-security environments: Designed with scenarios like medical access to patient data or secure storage devices in mind.
- Access tied to individual credentials: Ensures resource availability is linked directly to a specific user’s verified identity.
How it connects to US9251332B2?
- Both systems use proximity-based devices (e.g., transponders or digital keys) to enable or restrict access to computing resources.
- Each establishes a secure channel between a user-associated device and a host system based on pre-set credentials.
- The technologies share an emphasis on reducing manual authentication steps through background device recognition.
Why This Matters
This patent shows how access control methods have been tailored for real-time, high-security environments. Its reliance on automatic device recognition and secure channel creation parallels US9251332B2’s goals of delivering seamless, presence-based authentication in computing systems.
Related Read: Secure Matrix’s US8677116B1 shows how reusable identifiers streamline multi-factor authentication. It parallels US9251332B2’s focus on wireless credentials for protected environments.
#3. KR100478843B1
This Korean patent, KR100478843B1, published in 2005, introduces a wireless locking system for personal computers that operates based on the presence of a portable device broadcasting a unique RF code, enabling the PC only when the authenticated device is within a predefined range.
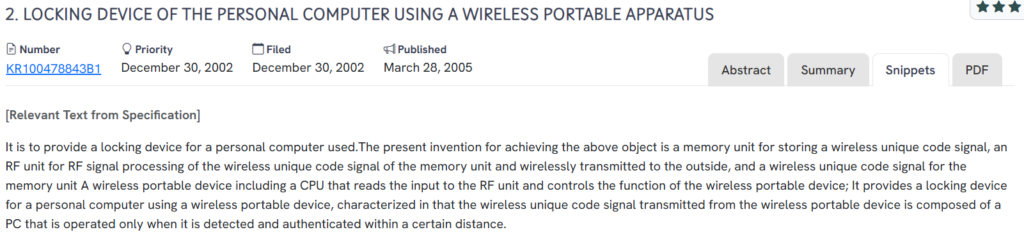
What This Patent Introduces To The Landscape
- Wireless RF-based locking mechanism: Uses a portable device that transmits a unique wireless code to control PC access.
- Proximity-based PC activation: The computer only operates when the authenticated portable device is detected within a specific distance.
- Integrated CPU-controlled wireless device: The portable unit features a processor that manages authentication signals and internal operations.
- Physical-layer security integration: Emphasizes hardware-level control over computer access, reducing dependence on software-only passwords.
How it connects to US9251332B2?
- Both systems use wireless portable devices to determine access eligibility based on proximity.
- Each employs unique identification codes to validate user presence before enabling functionality.
- Both patents aim to automate security without requiring user intervention at every login.
Why This Matters
This work highlights how early innovations tackled user authentication by embedding proximity and identity checks into hardware. It shares US9251332B2’s emphasis on seamless access control through device presence, reinforcing a move toward more intuitive and secure computing environments.
Note: Beyond who is granted access, some systems determine how access is granted. Quantion LLC and US7734283B2: Exploring Key Related Patents links content viewing to automated credentialing, unlocking hotspot internet without a paywall.
If you’re exploring how wireless access systems evolved into modern public hotspots, our analysis of US7734283B2 shows how ad-supported Wi-Fi turned sponsored content into seamless connectivity for everyday users.
#4. JP2000222289A
This Japanese patent, JP2000222289A, published in 2000, discloses a proximity-based information processing system where access to encrypted data is granted only when a certified wireless device, such as a wristwatch, is detected within range of a mobile computer.
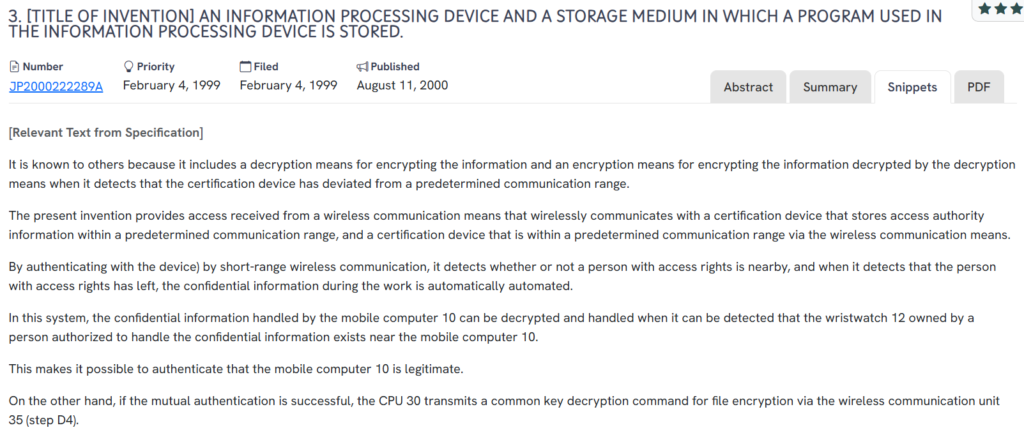
What This Patent Introduces To The Landscape
- Short-range wireless authentication: Access to sensitive information is controlled via close-proximity communication with a certified device.
- Automatic encryption upon departure: If the authorized device moves out of range, the system automatically re-encrypts active confidential data.
- Wearable authentication devices: Implements personal items like wristwatches as physical tokens for access validation.
- Mutual authentication and decryption logic: Requires two-way validation before granting decryption commands for secure files.
How it connects to US9251332B2?
- Both inventions use wireless proximity to determine whether a user has physical access rights to computing resources.
- Each emphasizes automatic security actions (like locking or encrypting data) when the user departs.
- Both systems rely on external, personalized authentication devices to control access at the hardware and data level.
Why This Matters
This patent reflects an early integration of wearable tech into secure access protocols. Like US9251332B2, it focuses on passive, location-based security management, minimizing user effort while enhancing protection for sensitive information.
For a deeper look at proximity-triggered wireless access, refer to our audit of US11095640B1.
Related Read: US7714726B2 and other patents fixed RFID’s bulk-reading issue with semi-transparent antennas. That same reliability challenge shows up in wireless access systems, where patents like US9251332B2 work to keep signals accurate even in proximity-heavy environments.
#5. CN101089869A
This Chinese patent, CN101089869A, published in 2007, discloses a method and apparatus for securing computer login using RFID technology, enabling a computer to authenticate users by comparing RFID tag data with pre-stored login credentials.
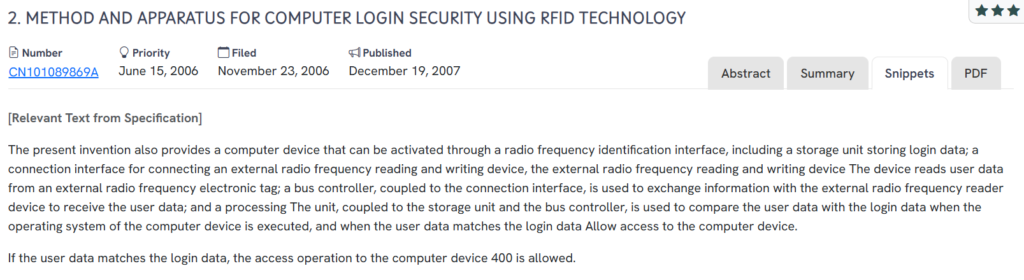
What This Patent Introduces To The Landscape
- RFID-enabled authentication system: Allows a computer to read login credentials from an external RFID tag.
- Secure login verification logic: Compares incoming RFID user data with stored credentials before permitting access.
- Hardware-based RFID interface: Integrates a connection and bus controller to manage communication with external RFID readers.
- Embedded access control logic: Grants or denies access at the system level, triggered automatically during OS execution.
How it connects to US9251332B2?
- Both systems utilize wireless identification (RFID or similar) to verify user presence and grant access.
- Each relies on stored credentials within a secure external device for login verification.
- Both automate authentication at the hardware interface level, minimizing manual user input.
Why This Matters
This patent demonstrates an RFID-based pathway to hands-free login authentication. Its approach closely mirrors the access logic of US9251332B2, reinforcing the role of external wireless devices in streamlining and securing user access to computing environments.
RFID-based login systems have evolved in parallel across regions. For additional insights into device-triggered authentication using RFID, check out our technical review of US7724143B2.
If you’re exploring how networks can authorize access without fixed billing models, the US7552870B2 patent offers a powerful example through its credit-based gateway exchange.
Note: Identity without exposure is a recurring theme. Personal Digital Key Patent explores cryptographic anonymity, paralleling US8577782B2’s semi-anonymous identifiers, balancing privacy with function.
How To Find Related Patents Using Global Patent Search
Understanding the broader patent landscape is essential when analyzing technologies tied to secure access, proximity-based authentication, or digital key systems. The Global Patent Search tool streamlines this process, enabling users to discover patents that share design logic, wireless security protocols, or device-triggered access control.
1. Enter the patent number into GPS: Start by entering a patent number like US9251332B2 into the GPS tool. The platform automatically interprets it into a structured query, which you can refine using terms like wireless authentication, physical token access, or encrypted login control.

2. Explore conceptual snippets: Rather than claim-by-claim analysis, GPS now surfaces key text snippets. These highlight how other systems handle device-triggered encryption, user presence detection, or hardware-linked access mechanisms.
3. Identify related inventions: The tool uncovers systems that use proximity signals, RFID tags, or digital keys to secure files, lock systems, or validate identities, offering a view into how similar challenges have been addressed.
4. Compare systems, not legal claims: GPS focuses on how systems function rather than their legal phrasing. This helps analysts uncover real-world design parallels without needing to navigate complex patent language.
5. Accelerate cross-domain insights: Whether you’re exploring cybersecurity, physical access devices, or secure computing workflows, GPS enables fast discovery of related technologies that may span consumer electronics, enterprise security, and beyond. See our analysis of digital token patents on how short-range authentication tools are evolving across platforms.
With this concept-first approach, Global Patent Search empowers engineers, researchers, and IP professionals to track innovation pathways, uncover overlaps, and guide strategic patent research more effectively.
Recommended Read: Vendor tokens aren’t just for content. US7177838B1 maps cleanly to access control. Issuers can mint prepaid, time-boxed tokens for doors, lockers, or devices without involving card networks.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.



