As digital ecosystems expand, certain patents gain renewed relevance, not because of legal disputes alone, but because the solutions they propose mirror today’s technological needs.
Patent US7203844B1 stands out for its approach to layered encryption, offering a recursive method for securing digital content in transit. It is now at the center of multiple infringement actions filed by Torus Ventures LLC, a non-practicing entity (NPE), targeting companies including Brinker International, Inc. and Briza, Inc.
In this article, we turn to the Global Patent Search (GPS) platform to identify related inventions that share conceptual ground with US7203844B1. Rather than dissect litigation details, we focus on identifying structurally similar patents using top features of the GPS tool and its snippet-based discovery engine.
If you’re in IP strategy, product development, or simply tracking innovation in digital rights management, this is an evidence-based look worth exploring.
Understanding Patent US7203844B1
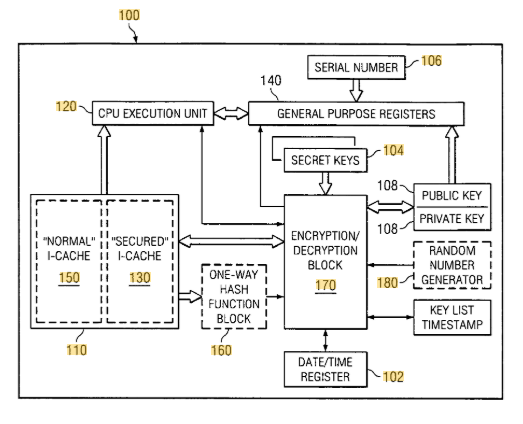
US7203844B1, titled “Method and system for a recursive security protocol for digital copyright control,” describes a security system that uses layered encryption to protect digital content. The method involves encrypting a bitstream multiple times, each with a different algorithm and paired decryption logic, creating a self-referential, recursive encryption process.
Source: Google Patents
Its Four Key Features Are
#1. Recursive encryption layers: A bitstream is encrypted once, then encrypted again along with its decryption method to create multiple secure layers.
#2. Decryption algorithm association: Each encrypted layer is linked to its corresponding decryption algorithm, ensuring controlled access and security.
#3. Self-encrypting protocol design: The protocol treats all digital data equally, including its own logic, allowing it to encrypt and update itself recursively.
#4. Flexible key management structure: Keys can be embedded in hardware, stored on servers, or managed through structured key data systems, including timestamped and count-limited access.
This design enables updates and enforcement without modifying the protected content. Its recursive nature also supports evolving encryption standards that can be layered over existing protections.
Related Read: Just as US7714726B2 and similar patents ensure dense RFID stacks remain readable, layered encryption patents focus on maintaining integrity when multiple signals overlap. Both prove how resilience under congestion shapes secure communication.
Similar Patents As US7203844B1
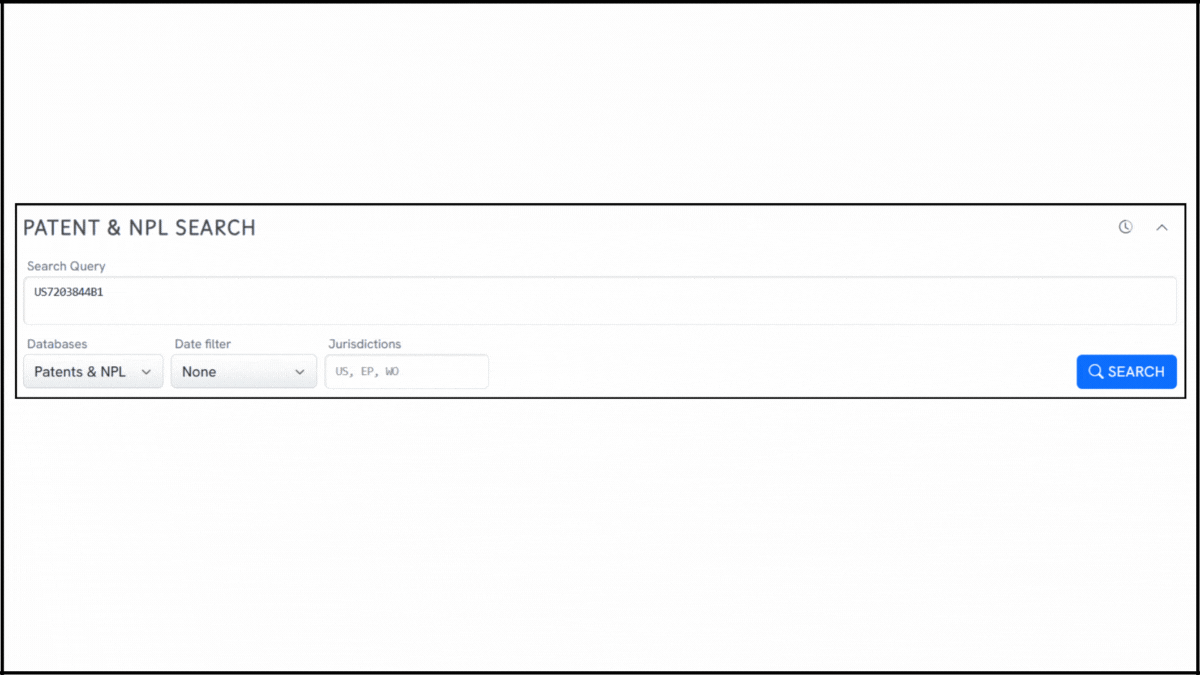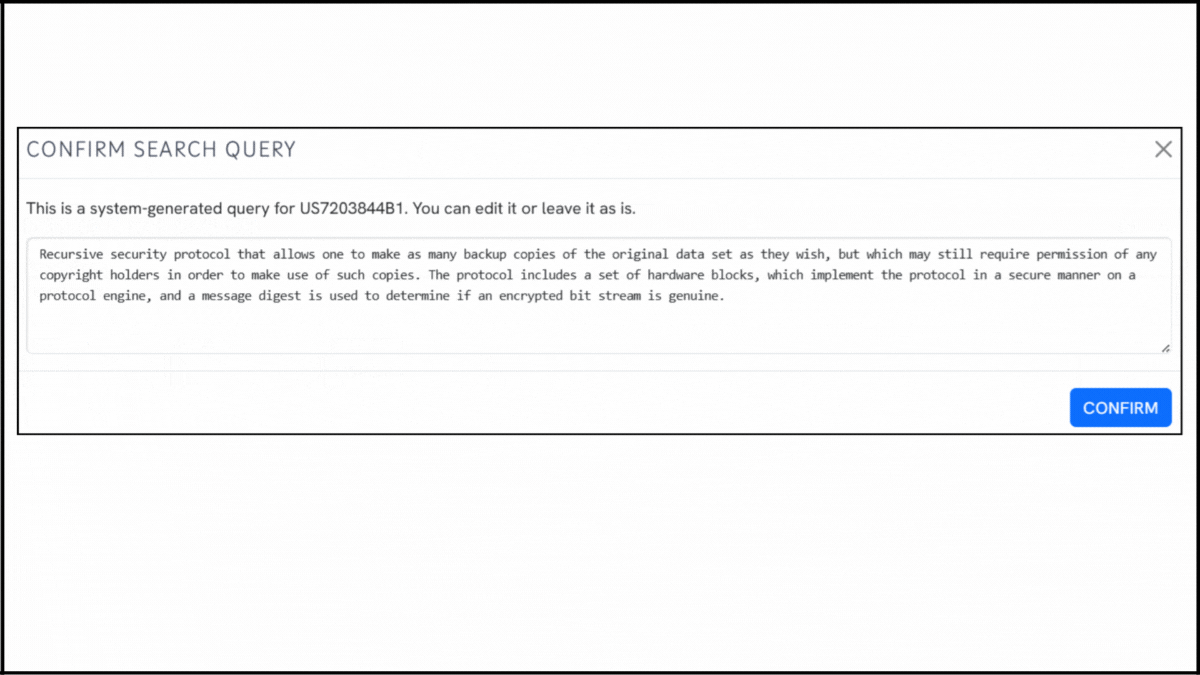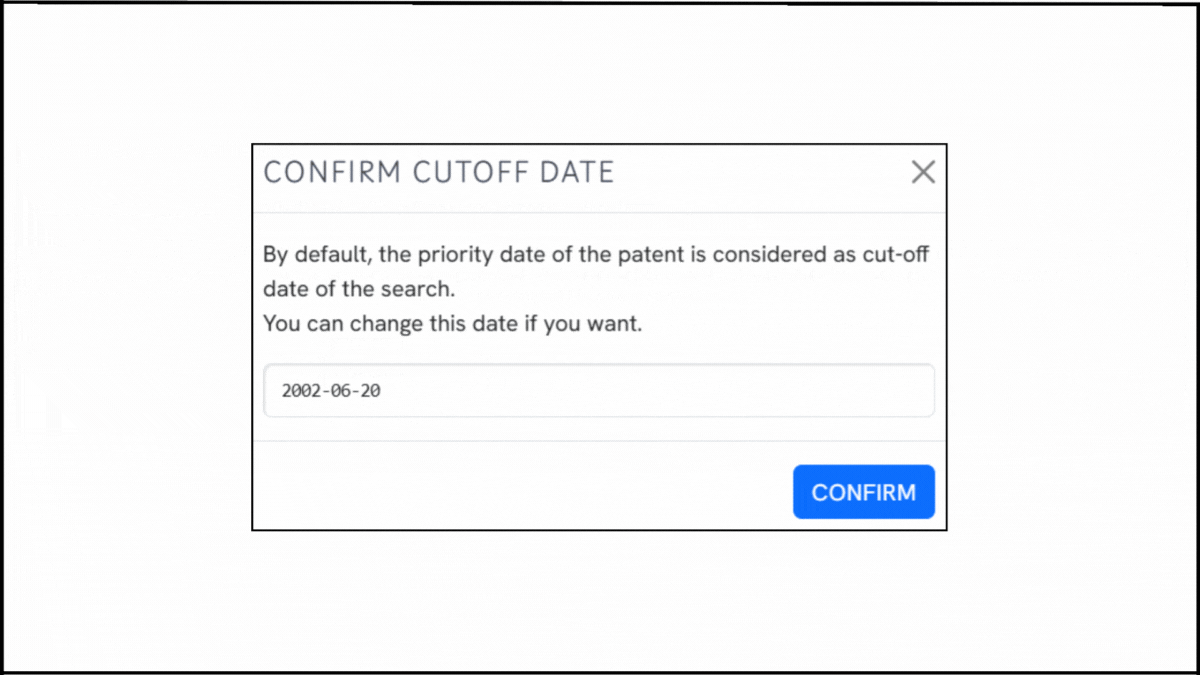
To explore the innovation landscape surrounding US7203844B1, we ran the patent through the Global Patent Search tool. Below is a quick glimpse of the GPS tool in action:
Source: Global Patent Search
This analysis surfaced a list of related patents that share technical similarities in recursive encryption, key management, and content protection. Below, we highlight five of these references that reflect comparable ideas in secure content delivery and digital rights enforcement. These examples offer insight into how similar challenges have been addressed across different frameworks.
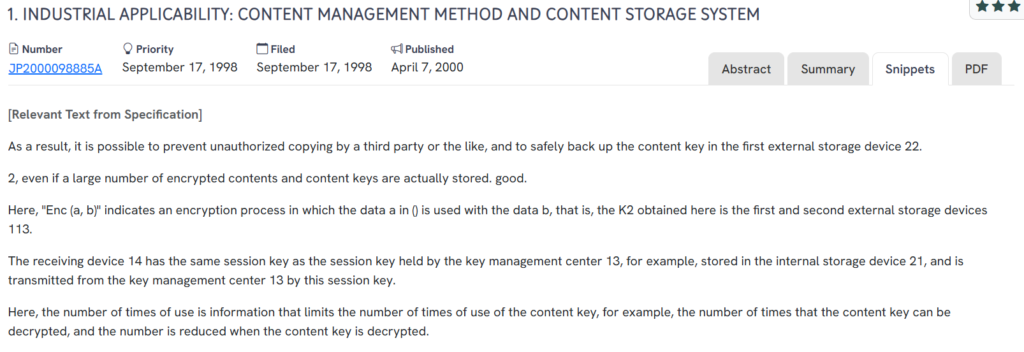
#1. JP2000098885A
This Japanese patent, JP2000098885A, published in 2000, outlines a content management and storage system designed to prevent unauthorized copying while enabling the secure handling and controlled use of encrypted content keys.
Source: GPS
What This Patent Introduces To The Landscape
- Session-based key verification – Establishes shared session keys between a receiving device and a central key management server to authenticate access.
- Decryption-use limitation – Introduces a mechanism that reduces the allowed number of decryptions each time a content key is used, effectively controlling how often content can be accessed.
- Encrypted backup of content keys – Enables secure storage and backup of encrypted keys across external devices to enhance redundancy and resilience.
- Nested encryption structure – Applies layered encryption operations where one key is encrypted using another, represented as “Enc(a, b),” aligning with recursive encryption logic.
How It Connects To US7203844B1
- Both patents emphasize layered encryption techniques to safeguard digital content.
- They share a focus on key pairing and session-bound access, ensuring only authorized decryption paths are enabled.
- JP2000098885A’s use-limited key model aligns with US7203844B1’s flexible, rule-based key management.
Why This Matters
This reference highlights early implementations of access-restricted encryption and external key redundancy, concepts that strengthen the foundation for recursive and self-reinforcing security protocols, as developed further in US7203844B1.
Trust-based filtering has appeared in other domains as well, including US9639608B2 , where layered decision logic determines when information should be revealed.
Related Read: Beyond transport security, some systems cryptographically bind billing data itself to prevent tampering. Our piece on US8005457B2 shows how layered verification and signed records harden cloud/service charging against fraud.
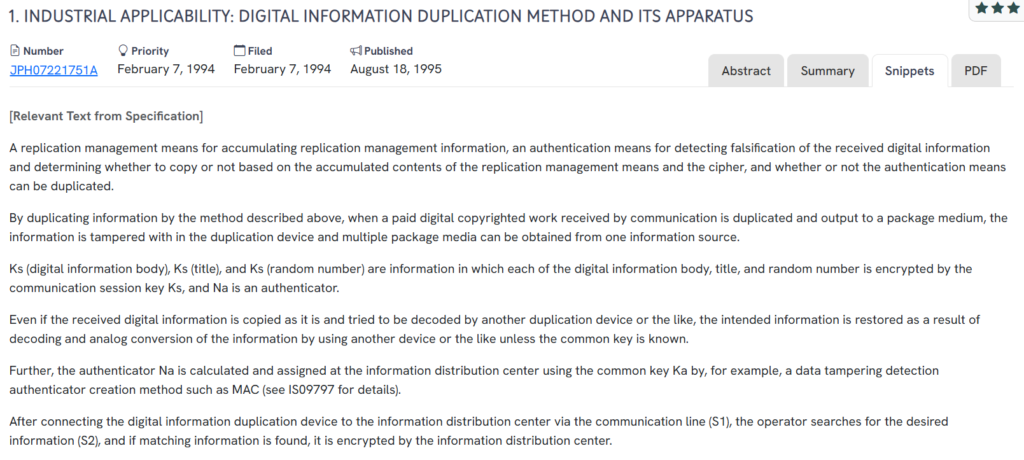
#2. JPH07221751A
This Japanese patent, JPH07221751A, published in 1995, outlines a system for duplicating digital information with built-in authentication and tamper detection. It focuses on controlling duplication of paid digital content through encryption and device-specific validation using session keys and message authentication codes.
Source: GPS
What This Patent Introduces To The Landscape
- Replication management with tamper detection – Uses an authentication mechanism to determine whether duplication is allowed based on cipher checks and stored replication rules.
- Encrypted session-based content handling – Encrypts individual content components (body, title, random number) using a session key to ensure device-specific decoding.
- Authenticator-based validation (Na) – Applies message authentication codes (MACs) for verifying content integrity, generated at the distribution center using a shared secret key.
- Controlled output to physical media – Prevents mass duplication by enabling content output only through authenticated sessions with the original distribution system.
How It Connects To US7203844B1
- Both patents implement layered encryption and session keys to ensure secure content delivery and usage control.
- They share a focus on authentication mechanisms that validate content and devices before decryption or duplication.
- The approach of restricting replication unless specific cryptographic conditions are met reflects a similar goal to US7203844B1’s recursive, rule-based access structure.
Why This Matters
This reference underscores the importance of combining encryption with authentication to manage digital rights. Its emphasis on device-specific decryption and tamper prevention anticipates the layered security logic that defines the recursive encryption system of US7203844B1.
Related Read: Secure transport is critical when chats are anonymous and ephemeral. Random Chat LLC: Exploring Related Patent Risks for US8402099B2 details how profile-controlled, real-time sessions ride over TCP/UDP with a privacy-first design.
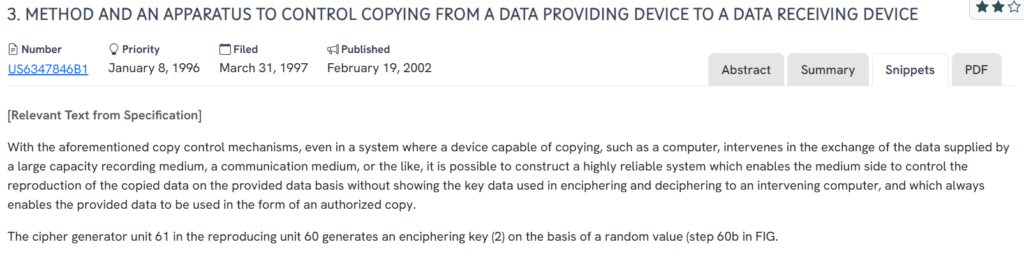
#3. US6347846B1
This U.S. patent, US6347846B1, published in 2002, outlines a method and apparatus for controlling the copying of data from a source device to a receiving device. It emphasizes secure content reproduction by concealing encryption keys from intermediary systems and ensuring only authorized copies are accessible.
Source: GPS
What This Patent Introduces To The Landscape
- Intermediary-proof copy protection – Prevents key exposure by ensuring encryption and decryption keys are not revealed to intermediary devices such as computers.
- Medium-side copy control – Grants the data-providing medium control over how and when content can be reproduced on receiving devices.
- Randomized key generation – Utilizes a cipher generator that produces encryption keys based on random values, enhancing unpredictability and content security.
- Authorized-use enforcement – Ensures that only verified, authorized copies of the data can be reproduced, even in the presence of potential bypass mechanisms.
How It Connects To US7203844B1
- Both patents emphasize controlled decryption environments that shield cryptographic operations from external tampering.
- US6347846B1’s method of key concealment aligns with US7203844B1’s recursive encryption model, which secures decryption logic within encrypted layers.
- The use of randomized key generation contributes to a layered, adaptive encryption structure comparable to that in US7203844B1.
Why This Matters
This patent highlights strategies to maintain secure, authorized content usage even in environments prone to interception or manipulation. Its architecture supports the broader principle of secure data access architectures encapsulated within protected encryption layers, a foundational concept also central to US7203844B1.
Did you know? Just as recursive key updates in US7203844B1 save processing overhead, US7057960B1 conserves energy by refreshing only active memory zones. Both show how selective operations drive efficiency.
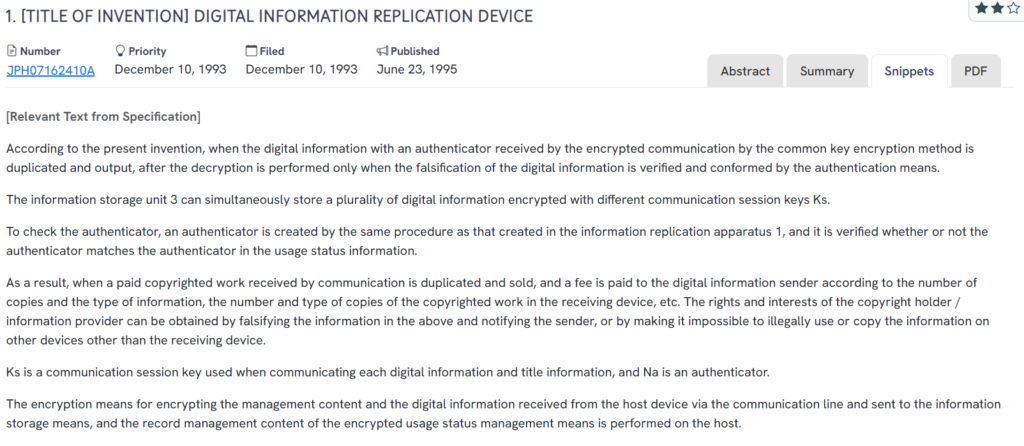
#4. JPH07162410A
This Japanese patent, JPH07162410A, published in 1995, outlines a digital information replication device that allows controlled duplication of encrypted content based on authentication checks. The system ensures that content is only decrypted and copied when its integrity is verified, while tracking usage to protect copyright interests.
Source: GPS
What This Patent Introduces To The Landscape
- Authentication-based decryption control – Decryption is performed only after verifying the integrity of digital information through an authenticator.
- Session key–segmented storage – The system supports storing multiple encrypted content items, each protected by different communication session keys.
- Usage tracking and fee reporting – Duplication events are logged, and usage status is uploaded to the distribution center to enable billing and prevent unauthorized replication.
- Device-bound content protection – Restricts copying and playback to the original receiving device, preventing redistribution through unauthorized hardware.
How It Connects To US7203844B1
- Both patents enforce content decryption through validation mechanisms, ensuring access only when integrity and authorization are confirmed.
- They utilize session key–based encryption to manage secure storage and controlled playback.
- JPH07162410A’s usage tracking and centralized monitoring echo the self-protecting, rule-governed structure introduced in US7203844B1.
Why This Matters
This patent showcases how encryption, authentication, and usage monitoring can be combined to protect digital works across distribution and duplication points. Its emphasis on secure session management and controlled replication reinforces key architectural ideas present in US7203844B1’s recursive security model.
#5. KR100655551B1
This Korean patent, KR100655551B1, published in 2006, outlines a method for handling digital literary works to safeguard copyrights. It introduces a system that uses authentication via a centralized copyright clearinghouse to manage access, prevent unauthorized duplication, and streamline distribution with user-specific identifiers.
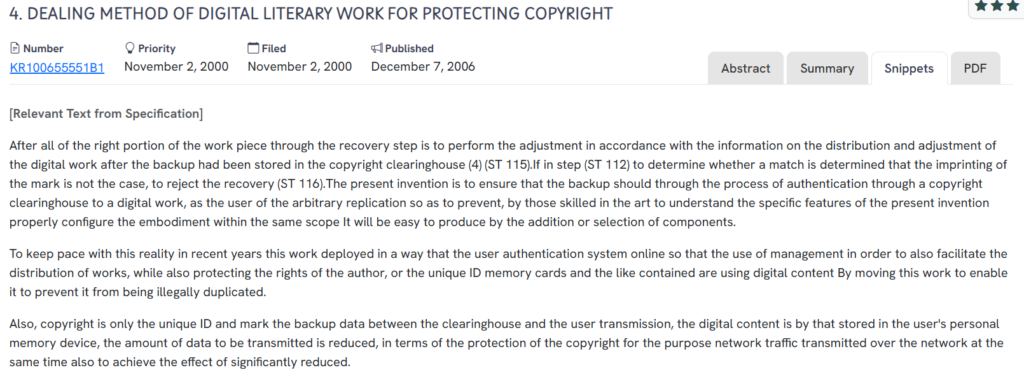
Source: GPS
What This Patent Introduces To The Landscape
- Clearinghouse-based authentication – Requires digital works to pass through a copyright clearinghouse for verification before recovery or duplication is permitted.
- Imprint verification and recovery rejection – Uses digital marks and IDs to determine whether content recovery should proceed or be denied.
- Unique ID–bound content management – Ties digital content to unique memory cards or personal storage devices, ensuring content cannot be copied arbitrarily.
- Optimized network distribution – Reduces network traffic by transmitting only ID and verification data between the user and the clearinghouse while keeping full content on the local device.
How It Connects To US7203844B1
- Both systems incorporate authentication-based access control, ensuring that content is only accessible when identity or verification protocols succeed.
- The use of external validation (clearinghouse) aligns with US7203844B1’s principle of layered, rule-based access and management.
- KR100655551B1’s emphasis on tamper-resistant, user-specific distribution reflects similar goals of controlled, encrypted delivery found in US7203844B1.
Why This Matters
This approach reinforces the value of centralized authentication and device-specific controls in managing digital content rights. Its layered structure and user-linked protection echo the recursive and modular encryption strategies central to US7203844B1.
Note: Just as recursive keys in US7203844B1 reduce overhead in secure exchanges, US7177838B1 lowers transaction costs through vendor-issued tokens. Both patents focus on efficiency in digital trust.
How To Find Related Patents Using Global Patent Search
Understanding the broader innovation landscape surrounding a patent like US7203844B1 is crucial for advancing secure content delivery, refining encryption frameworks, or benchmarking digital rights management systems. The Global Patent Search tool streamlines this process by surfacing inventions that share similar encryption architectures or key management strategies. Here’s how it works:
1. Enter the patent number into GPS: Start by entering a patent number, like US7203844B1, into the GPS search bar. The platform instantly generates a concept-aware query, which you can fine-tune with terms related to encryption, digital rights, or key control.

2. Explore conceptual snippets: Instead of listing claim-by-claim matches, GPS highlights intelligent text snippets that reveal how other patents approach similar challenges, such as recursive encryption, layered protection, or authenticated access.

3. Identify related inventions: The tool brings forward patents with shared ideas, like multi-key architectures, distributed decryption logic, or session-bound control, helping users track the evolution of secure data systems.
4. Compare frameworks, not just claims: GPS focuses on functional logic and system architecture. It lets users examine how encryption protocols behave across different inventions without requiring legal interpretation.
5. Accelerate insight across domains: Whether you’re working on DRM systems, cybersecurity protocols, or content authentication methods, GPS helps uncover technical overlaps that might otherwise go unnoticed.
With this functionality, Global Patent Search provides engineers, researchers, and IP strategists with a concept-first view of related patents, enabling better design decisions and more informed IP analysis.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.



