While some patents zero in on highly specific technical tweaks, others confront challenges that affect the internet at scale. US7523497B2 belongs to that second group.
Now featured in PacSec3, LLC v. Corero Network Security, Inc., this patent introduces a distributed method to counter packet flooding; an early, coordinated approach to limiting denial-of-service attacks by managing data flow at both sites and routers.
In this article, we turn to the Global Patent Search (GPS) platform to explore similar technologies. Rather than diving into legal claims, our focus is on identifying conceptually related systems that aim to monitor, filter, or suppress malicious traffic. If you work in network security, innovation strategy, or patent research, this data-driven look offers valuable insight into the broader landscape surrounding US7523497B2.
Understanding Patent US7523497B2
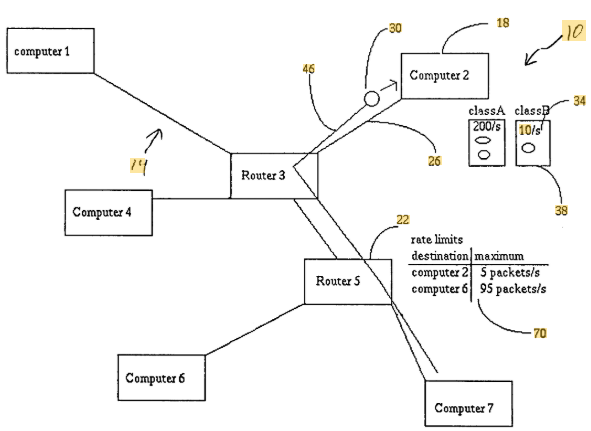
US7523497B2, titled “Packet Flooding Defense System,” presents a method to mitigate denial-of-service (DoS) attacks, specifically those involving packet flooding. The core idea is to use a distributed defense mechanism that enlists both host systems and routers to identify, classify, and restrict the flow of undesirable or malicious data.
The system allows hosts to signal routers about unwanted traffic sources and request that data rates be limited accordingly. This helps conserve network bandwidth and ensures fair resource allocation across legitimate users.
Source: Google Patents
Its Four Key Features Are
#1. Cooperative defense framework: Participating sites and routers form a “cooperating neighborhood” that shares packet path data to better track and control traffic flow.
#2. Rate limiting based on packet classification: Hosts and routers classify packets into “wanted” and “unwanted” types and assign processing or forwarding limits to each class.
#3. Path-based filtering: Routers attach path information to packets, enabling recipients to trace data origins and apply selective rate control based on non-attacker-controlled metadata.
#4. Resource protection across network layers: The system can throttle packet rates not just at hosts, but also between routers and firewalls, reducing exposure at multiple points in the network.
This technology enables routers and hosts to coordinate traffic filtering using attacker-independent path data. It helps reduce unwanted traffic before it overwhelms networks.
Related Read: US7714726B2 solved interference in RFID by letting energy pass through tags. Network defense patents like US7523497B2 tackle a parallel problem. Both patents ensure communication flows even when systems are under heavy strain.
Similar Patents As US7523497B2
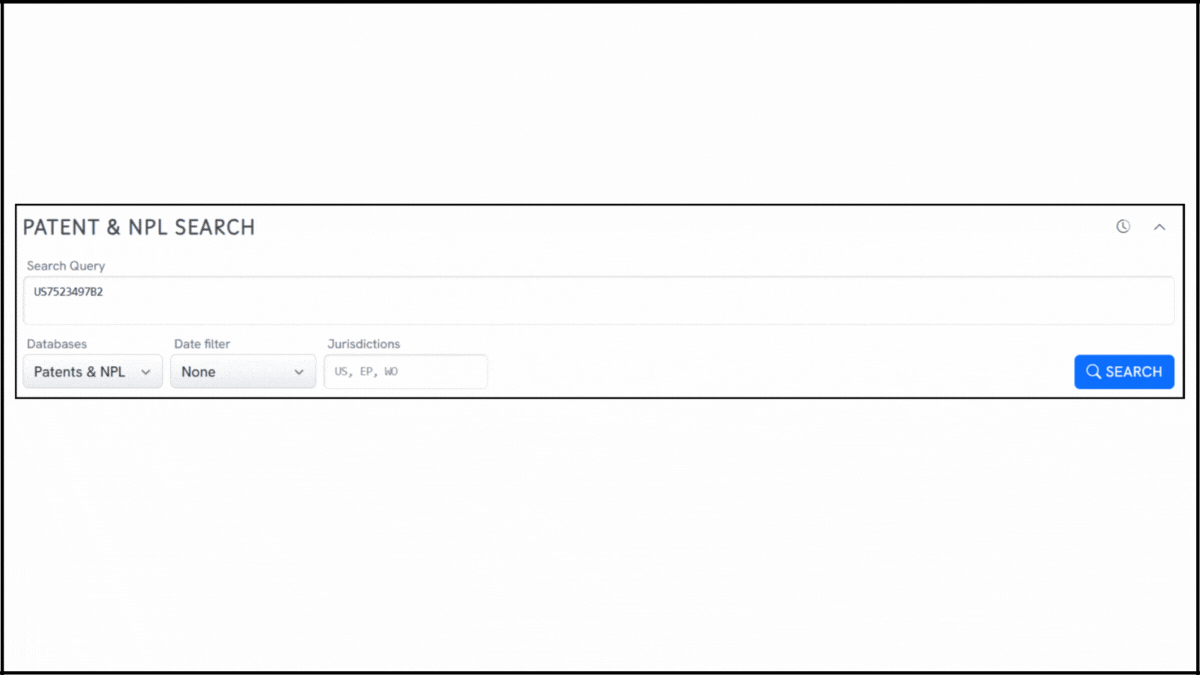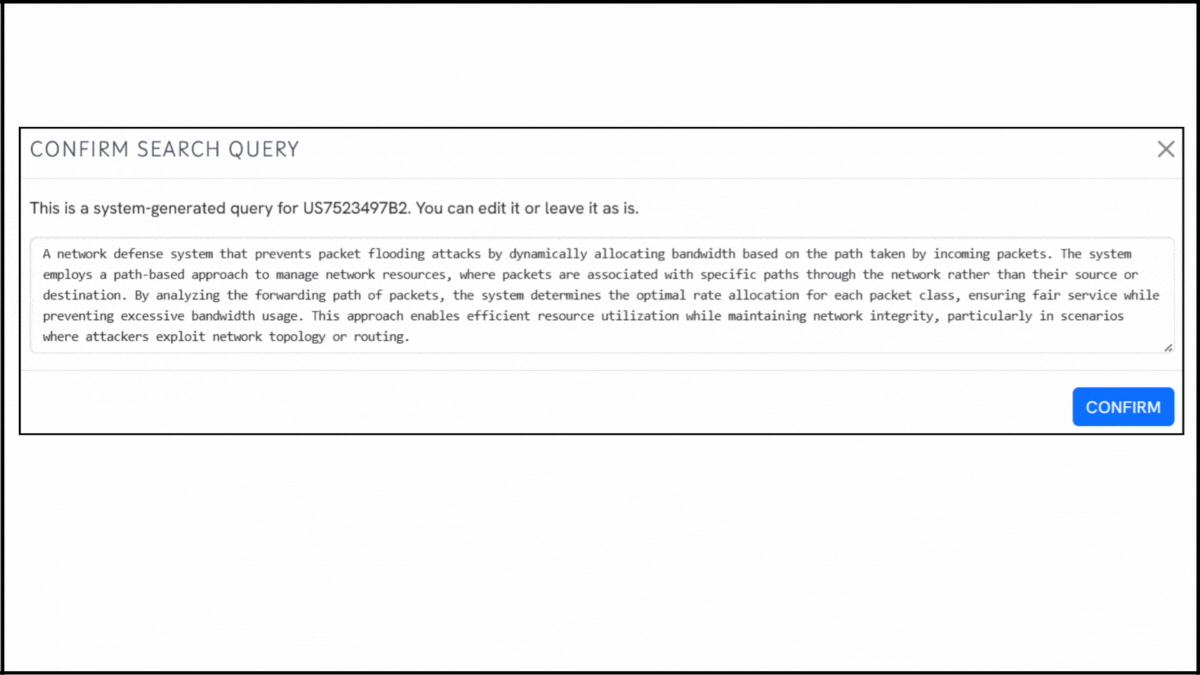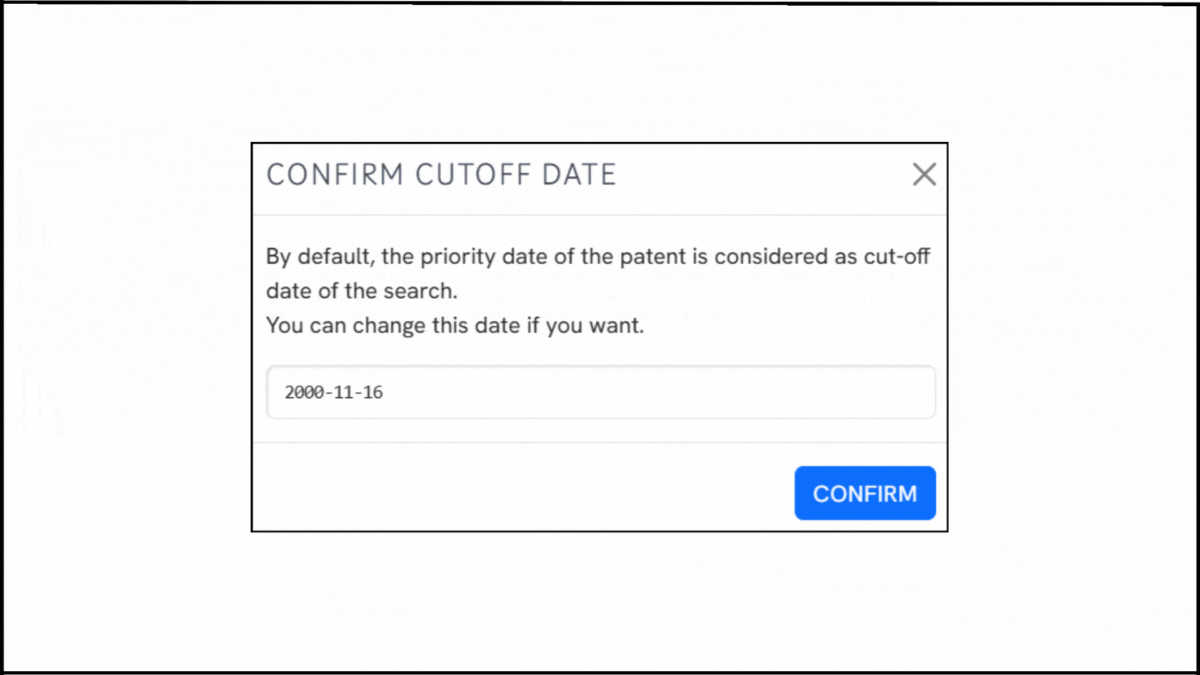
To explore technologies conceptually aligned with US7523497B2, we used the Global Patent Search (GPS) tool. Below is a quick glimpse of the GPS tool in action:
Source: Global Patent Search
This analysis revealed several patents addressing unwanted data filtering, bandwidth throttling, and dynamic traffic management across network systems. These references provide a closer examination of how similar challenges have been addressed through various architectures and control mechanisms.
#1. JP2002044136A
This Japanese patent, JP2002044136A, published in 2002, introduces a flow control device for routers that filters traffic by protocol type and controls bandwidth usage per application service.
Source: GPS
What This Patent Introduces To The Landscape
- Protocol-level filtering – Blocks all protocols and services except those with approved bandwidth allocation.
- Cycle-based traffic monitoring – Measures packet flow in defined time cycles and resets metrics for bandwidth recalibration.
- TCP port prioritization – Uses IP headers and TCP port data to enable differentiated packet handling and routing control.
- Congestion management – Prevents overflow by adjusting packet transmission rights based on real-time usage.
How It Connects To US7523497B2
- Both systems filter unwanted or excess traffic before it reaches bandwidth limits.
- Each uses internal routing logic to enforce flow control under congestion.
- They aim to maintain fair resource use by dynamically adjusting packet handling.
Why This Matters
This early design shows how packet filtering and protocol-based throttling can shape network behavior, principles echoed in US7523497B2’s distributed flood defense system.
Related Read: For a deeper look at how networks verify the integrity of data packets, you can also explore our analysis of US7895643B2, a patent that introduced cryptographic trust signals directly into packet flows.
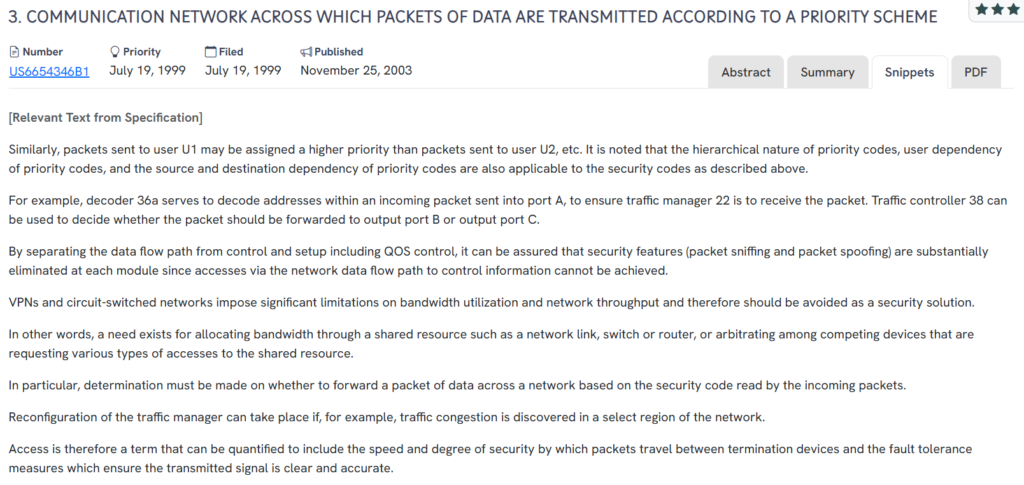
#2. US6654346B1
This U.S. patent, US6654346B1, published in 2003, introduces a priority-based packet routing system that combines quality-of-service control with layered security mechanisms across shared networks.
Source: GPS
What This Patent Introduces To The Landscape
- Priority-based data transmission – Packets are ranked based on destination, source, or user, influencing how bandwidth is allocated.
- Integrated security layers – Security codes and identification modules restrict packet access, reducing spoofing and sniffing risks.
- Dynamic traffic control – Traffic managers can reconfigure packet flow in response to congestion or access conditions.
- Separated control paths – Control and data flows are isolated to improve fault tolerance and prevent interference with routing logic.
How It Connects To US7523497B2
- Both aim to regulate packet flow through dynamic, rule-based traffic decisions.
- Each introduces mechanisms for distributed control across routers or modules.
- Both systems balance bandwidth fairness with the need to filter or throttle data traffic.
Why This Matters
This reference highlights early efforts to blend traffic prioritization with built-in network defenses, key concepts echoed in US7523497B2’s coordinated DoS protection strategy.
The same idea surfaces again in US11736499B2, where unexpected shifts in an application’s execution flow are treated as early signals of possible injection behavior.
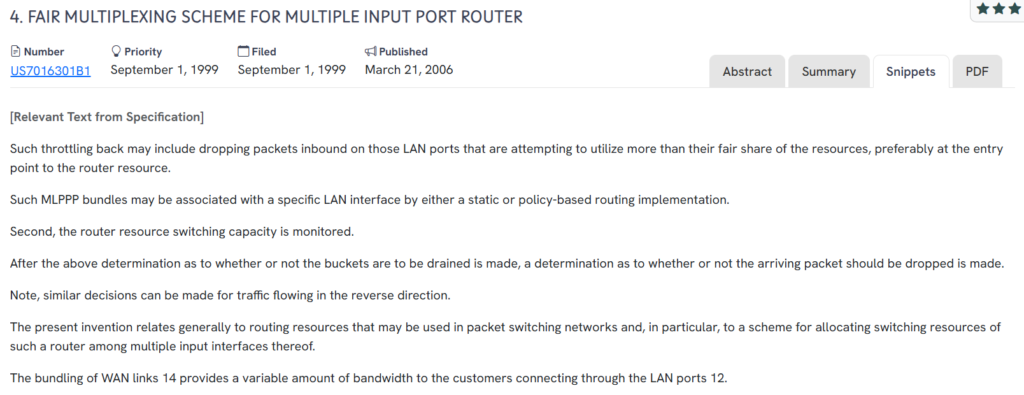
#3. US7016301B1
This U.S. patent, US7016301B1, published in 2006, introduces a fair multiplexing scheme for routers handling data from multiple input ports to ensure balanced bandwidth allocation.
Source: GPS
What This Patent Introduces To The Landscape
- Fair resource allocation – Detects overuse from specific LAN ports and drops excess packets at the router entry point.
- Input-based throttling – Monitors inbound traffic per interface and enforces limits to avoid congestion and resource monopolization.
- Dynamic bandwidth control – Supports variable bandwidth by bundling WAN links and allocating switching capacity based on usage.
- Two-way flow regulation – Applies traffic control logic to both inbound and outbound packet streams.
How It Connects To US7523497B2
- Both monitor incoming packet flow and selectively drop data to preserve fair access.
- Each manages router resources through distributed bandwidth enforcement.
- They seek to contain overload risks by applying intelligent throttling early in the data path.
Why This Matters
This work strengthens the concept of early-stage packet filtering and equitable bandwidth sharing, core tactics in US7523497B2’s distributed flood defense model.
Just as network defenses evolve to support new architectures, telephony systems also need adaptive bridging solutions. Our analysis of US11974173B2 explains how legacy analog phones are connected to LTE voice networks using a dedicated VoLTE adapter.
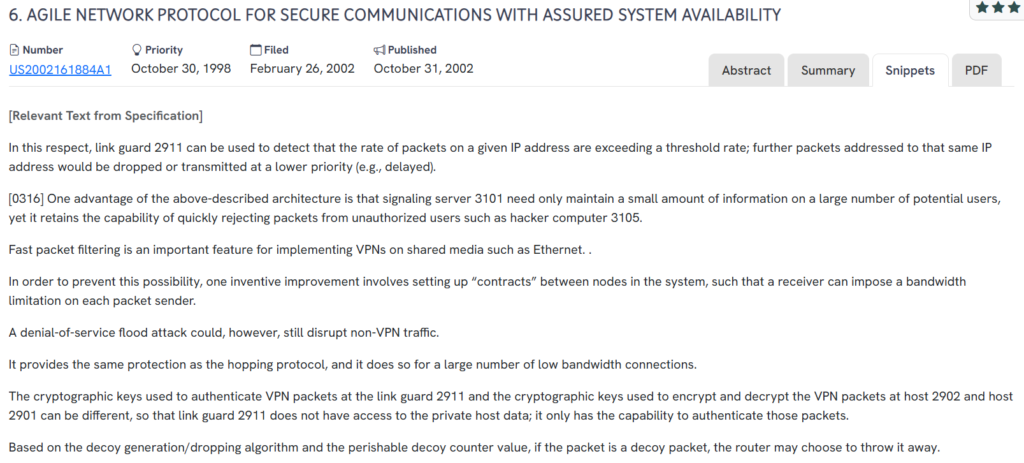
#4. US20020161884A1
This U.S. patent, US20020161884A1, published in 2002, introduces an agile routing protocol that enhances secure communications while mitigating denial-of-service threats through bandwidth control and decoy packet strategies.
Source: GPS
What This Patent Introduces To The Landscape
- Rate-based packet filtering – Drops or delays packets when traffic exceeds predefined thresholds at specific IP addresses.
- Receiver-imposed bandwidth limits – Uses contract-based enforcement to prevent any sender from exceeding allowed traffic rates.
- Decoy packet handling – Inserts and filters dummy data to resist traffic analysis and reduce vulnerability to targeted attacks.
- Agile routing and address hopping – Randomizes IP routes and addresses to enhance redundancy and resist packet-level surveillance.
How It Connects To US7523497B2
- Both prioritize network availability by filtering or slowing excess traffic.
- Each enables destination-controlled rate management across the network.
- They apply distributed filtering logic to reduce DoS and spoofing risks.
Why This Matters
This system reinforces how adaptive filtering and endpoint control can defend against packet floods, aligning closely with US7523497B2’s coordinated mitigation approach.
Recommended Read: While this invention focuses on network protection, a related patent audit of US9584633B2 explores how optimizing packet flow and address switching can make communication layers inherently faster and more resilient under heavy traffic.
#5. JP2004503146A
This Japanese patent, JP2004503146A, published in 2004, introduces a content-aware network defense that assigns packets to lower-priority queues or drops them based on validation, session data, and flow signatures.
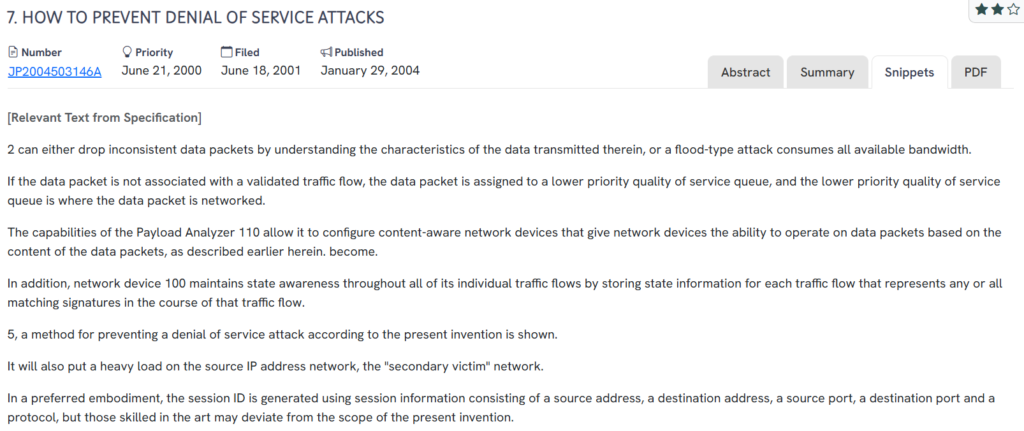
Source: GPS
What This Patent Introduces To The Landscape
- Session-based packet validation – Uses session IDs (source/destination/port/protocol) to track and verify legitimate traffic flows.
- Content-aware routing – Analyzes payloads and directs packets based on internal data, improving filtering accuracy.
- Priority queue management – Unvalidated or unknown packets are sent to low-priority queues or dropped outright.
- Stateful traffic tracking – Maintains flow state across the network to detect anomalies or attack patterns.
How It Connects To US7523497B2
- Both drop or downgrade suspicious traffic before it consumes resources.
- Each uses distributed devices to identify and react to packet-level threats.
- They manage traffic fairness using flow-based or content-aware logic.
Why This Matters
It shows how integrating content analysis and session tracking strengthens denial-of-service defenses, key elements that align with US7523497B2’s distributed mitigation model.
A deeper look at dynamic authentication in wireless networks can be found in our analysis of US7233664B2, which focuses on continuously regenerated encryption keys and synchronized authentication across network nodes.
How To Find Related Patents Using Global Patent Search
Understanding the broader patent landscape is key when tackling network security, bandwidth control, or denial-of-service mitigation. The Global Patent Search tool streamlines this process, helping users identify systems that reflect similar traffic management or router-level defense mechanisms.
1. Enter the patent number into GPS: Start by entering a patent number like US7523497B2 into the GPS tool. The platform transforms it into a smart query, which you can refine using terms like packet filtering, router coordination, or bandwidth throttling.

2. Explore conceptual snippets: Instead of comparing features claim-by-claim, GPS now offers curated text snippets. These highlight how other systems manage packet flows, prioritize data, or guard against overload conditions.

3. Identify related inventions: The tool reveals patents that tackle unwanted traffic, enforce flow control, or balance load across routers, showing how related problems have been approached over time.
4. Compare systems, not legal claims: Rather than focusing on formal legal language, GPS compares system behaviors. This helps users trace functional overlaps without navigating legal boundaries.
5. Accelerate cross-domain insights: Whether you’re working in cybersecurity, router architecture, or network optimization, GPS lets you uncover related ideas across technical domains that may otherwise be hard to connect.
With this approach, Global Patent Search gives analysts, engineers, and IP teams a structured, concept-first way to explore related technologies and inform smarter strategies.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.