Some technologies operate quietly in the background. Others shape how digital data is stored, accessed, and shared. US9465913B1 is part of that second group.
Recently mentioned in the case of Web 2.0 Technologies, LLC et al v. Methodist Hospital Hill Country, the patent has sparked renewed technical interest. It outlines a method for controlling access to personal information based on authorization levels and delivering updates that take effect at future dates.
Rather than focusing on legal arguments, we turn to the Global Patent Search (GPS) tool to examine related systems with similar design goals. These include structured data control, role-based access, and secure communication between authorized parties. Through this lens, we can gain a better understanding of how comparable technologies manage sensitive information within dynamic digital environments.
Whether you’re in digital health, secure communication, or data infrastructure, this mapped overview offers practical insights. It reveals how similar patterns continue to influence the broader technology landscape surrounding secure personal information management.
Understanding Patent US9465913B1
US9465913B1 describes a secure system for storing and distributing personal information through an online platform. The method allows users to enter personal data, assign varying levels of access security, and authorize specific parties to retrieve selected portions. The system also supports setting future-effective updates and notifying recipients about pending or completed changes.
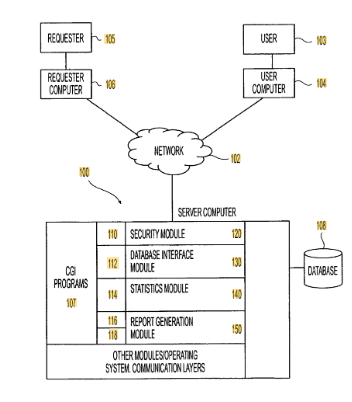
Source: GPS
Its four key features are:
#1. Security classification for data: Each information object is assigned a classification level that determines who can access it.
#2. Role-based data access: Requesters receive only the information they are authorized to see, based on identity and pre-approved permissions.
#3. Future-dated updates: Changes to stored data can be scheduled to take effect at a future time, with alerts sent to authorized parties.
#4. Comprehensive access logging: Every data request or update is recorded to create a full audit trail of system activity.
This patent addresses a critical need in managing personal information securely across digital systems. By combining granular access control, update scheduling, and complete traceability, it provides a robust framework applicable to sectors such as healthcare, finance, and secure communications.
For another deep dive into recursive encryption and flexible key control, see our analysis of similar protocols in US7203844B1.
Similar Patents As US9465913B1
To explore the innovation landscape surrounding US9465913B1, we used the Global Patent Search tool to surface related patents. Below is a quick glimpse of the GPS tool in action:
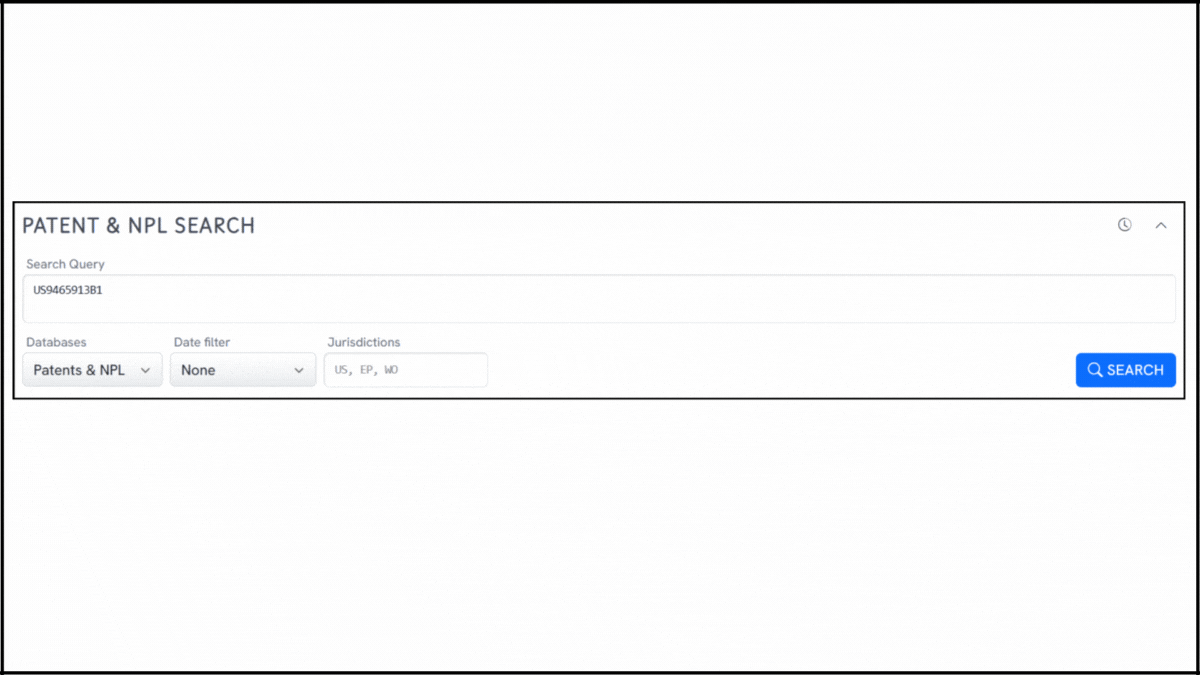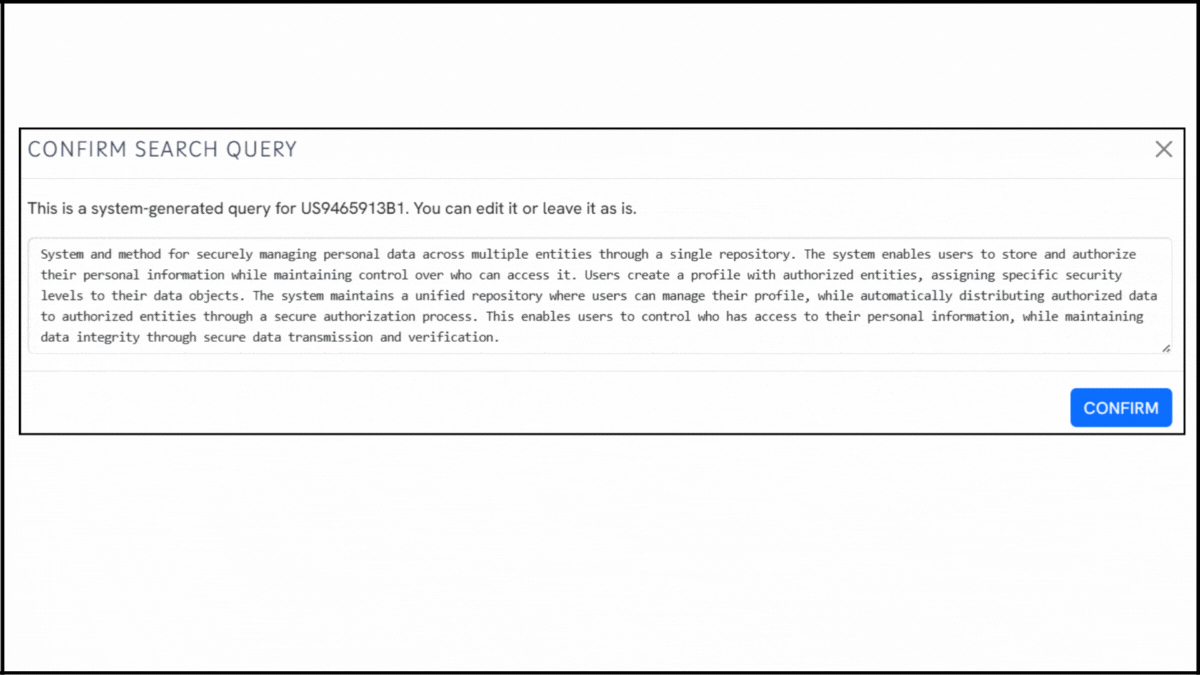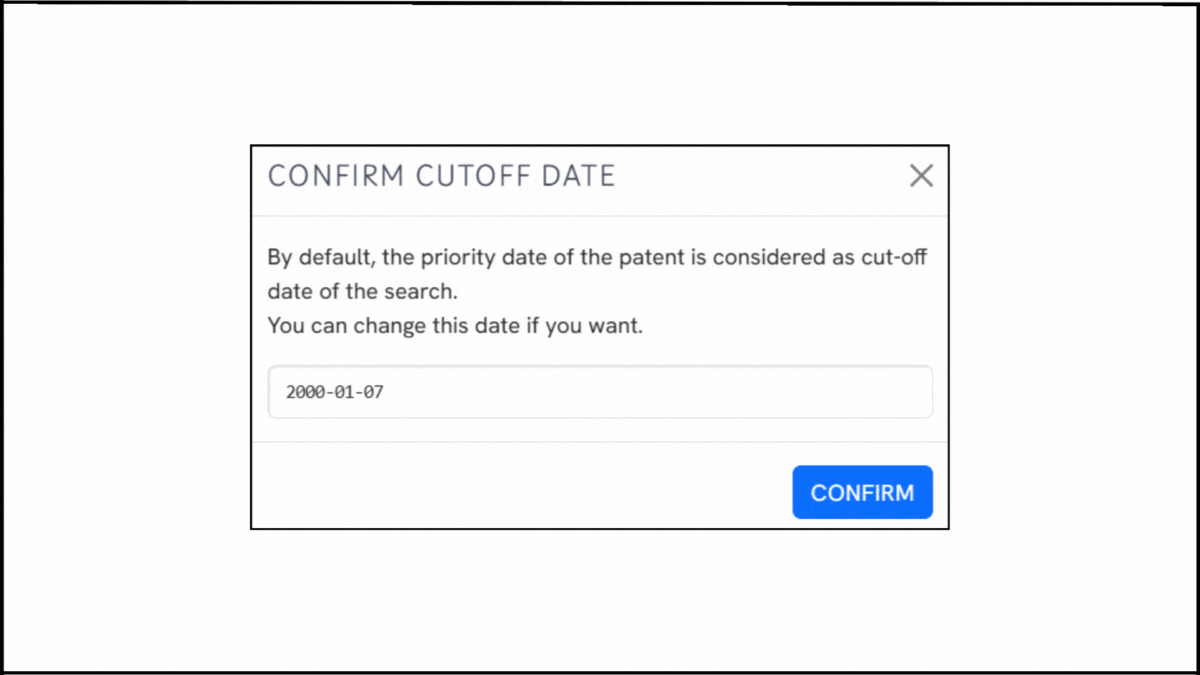
Source: GPS
This tool reveals technologies with overlapping functionality in secure information access, permission control, and personal data repositories. The following references highlight comparable ideas in credential-based access, user-controlled permissions, and structured update mechanisms.
#1. US9864877B1
This US patent, US9864877B1, published in 2018, builds on the concept of a secure personal data system by giving users granular control over how their stored information is accessed, viewed, or modified. It introduces advanced authorization mechanisms and layered security options that enable selective visibility and real-time permission handling, all while maintaining a complete audit trail of activity.
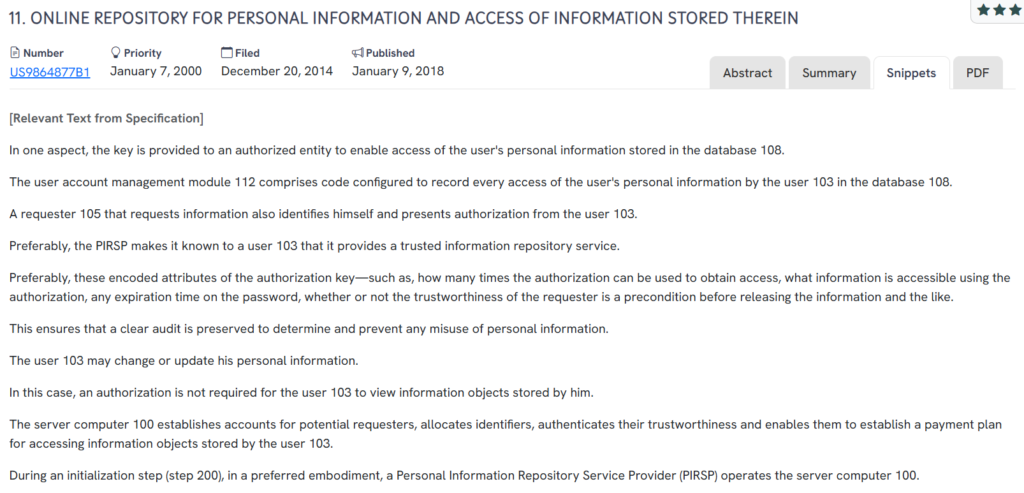
Source: GPS
What does this patent introduce to the landscape?
- Authorization key distribution: Keys can be configured for expiration, limited use, or conditional access depending on the trust level of the requester.
- Audit trail logging: Every user and requester interaction is recorded, helping ensure accountability and prevent misuse.
- Requester trust verification: The system authenticates requesters before allowing access, based on the provided identity and authorization.
- Selective content visibility: Permissions define what a requester can do, view, annotate, or edit, and to what extent.
- Directory-level security: Users can organize data in protected directories that are password-locked or hidden entirely from unauthorized users.
How does it connect to US9465913B1?
While US9465913B1 outlines a method for classifying and distributing personal data, US9864877B1 expands on real-time control over requester access. Both systems emphasize secure delivery, dynamic permissions, and detailed audit trails. Together, they reflect a shared vision for controlled, user-managed data dissemination:
- Key-based authorization with customizable control levels
- Identity-verification mechanisms tied to user-defined permissions
- Continuous logging and accountability across all data access operations
Why does this matter?
US9864877B1 emphasizes the evolution of permission-based data systems, where users can finely manage who sees what, and when. It reinforces design priorities that align with US9465913B1, transparent access control, user autonomy, and system-level accountability, offering deeper insight into how secure data repositories have matured over time.
If you’re exploring how modern systems detect abnormal execution behaviour inside applications, you may also want to look at US11736499B2, which focuses on identifying injection attacks through behaviour drift rather than signature patterns.
#2. JP2002517812A
This Japanese patent JP2002517812A, published in 2002, introduces a security framework for managing individual data access on a network. It emphasizes user authorization, identity verification, and encrypted data handling as part of a broader method for regulating digital access. The invention grants sole authority to the individual over their personal information, aligning with modern principles of data sovereignty.
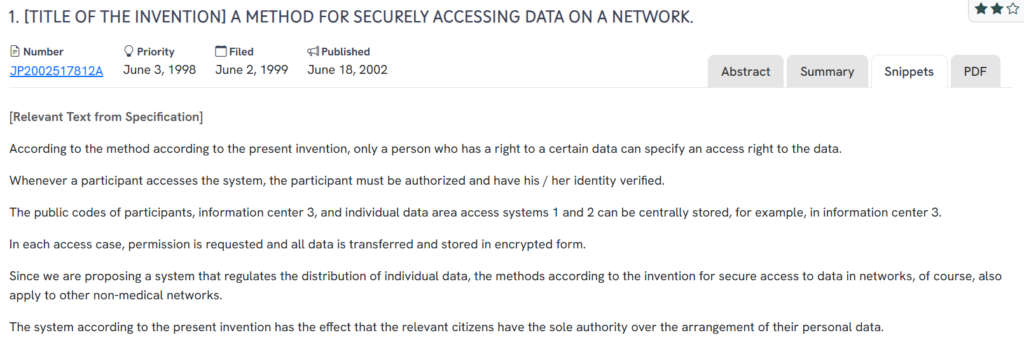
Source; GPS
What does this patent introduce to the landscape?
- User-controlled access rights: Only authorized individuals can define who has permission to view or interact with their data.
- Mandatory identity verification: Every system interaction requires participant biometric authentication to validate identity before access is granted.
- Centralized public key storage: Key infrastructure for users and systems is centrally managed, simplifying access control mechanisms.
- Encrypted data exchange: All data is transferred and stored in encrypted form to prevent unauthorized interception or tampering.
- Cross-domain applicability: Though designed with healthcare in mind, the method is adaptable to broader, non-medical network environments.
Another view on network-level traffic control can be seen in how other inventions address packet flooding, such as PacSec3’s US7523497B2.
How does it connect to US9465913B1?
While US9465913B1 focuses on classifying personal data and managing its release through role-based access, JP2002517812A presents a robust identity verification framework. Both patents prioritize user-defined control, encrypted communication, and traceable access conditions to protect sensitive data. Together, they support a model of secure data management centered on end-user governance and trusted authentication.
- Key-based access rooted in individual control
- Enforced identity verification for each transaction
- Data storage and transfer protected through encryption
Why does this matter?
JP2002517812A offers foundational insight into secure data exchange protocols, reflecting the same trust-driven approach seen in US9465913B1. It reinforces the notion that user authorization and system-wide encryption are critical components in the evolution of personal data repositories. This reference highlights the global convergence on technical standards for privacy-first digital infrastructures.
#3. JP2000076193A
This Japanese patent JP2000076193A, published in 2000, outlines a system for secure electronic information sharing based on tenant-based access restrictions. It introduces user lists, tenant validation steps, and multi-level permissions to control which individuals can view shared data. The method ensures that data access is strictly confined to authorized users within a defined tenant group, reflecting a compartmentalized security structure.
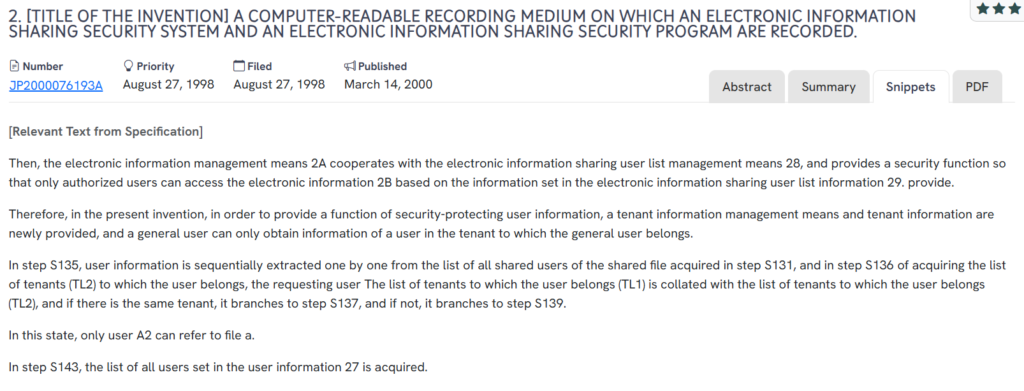
Source: GPS
What does this patent introduce to the landscape?
- User list-based access control: Only users explicitly listed in the access configuration can retrieve or view specific electronic information.
- Tenant-specific authorization: Users are grouped by tenant, and can only view information created or owned by others in the same tenant.
- Hierarchical permission checks: A multistep process verifies whether the requesting user’s tenant matches that of the information’s owner.
- Granular file restrictions: Individual files are locked down so that only designated users, such as “user A2”, can access them.
- Dynamic user validation: Access routines compare multiple user-tenant relationships to confirm eligibility in real time.
How does it connect to US9465913B1?
While US9465913B1 manages personal data distribution through security classifications and authorized requests, JP2000076193A focuses on limiting access through tenant validation and user listings. Both emphasize strict permission gating and role-aligned access. Their shared reliance on controlled user groups, validation layers, and data access boundaries showcases a parallel security architecture.
- Role-based visibility through explicit user associations
- Tenant-level compartmentalization of access rights
- Data availability limited by group-based authorization filters
Why does this matter?
JP2000076193A illustrates how access boundaries can be enforced using tenant models and user group logic. Like US9465913B1, it promotes precision control over who can interact with specific data. This tenant-based framework adds another dimension to the secure information-sharing conversation, demonstrating how layered, identity-driven access rules can protect sensitive content within multi-user environments.
#4. US5414844A
This U.S. patent, US5414844A, published in 1995, presents a framework for managing access to multiple data objects using a centralized authorization structure. It introduces mechanisms to define default access for unlisted users, along with explicit permissions for identified users. The method enables scalable access control across a large dataset through shared profiles and fine-tuned authority levels.
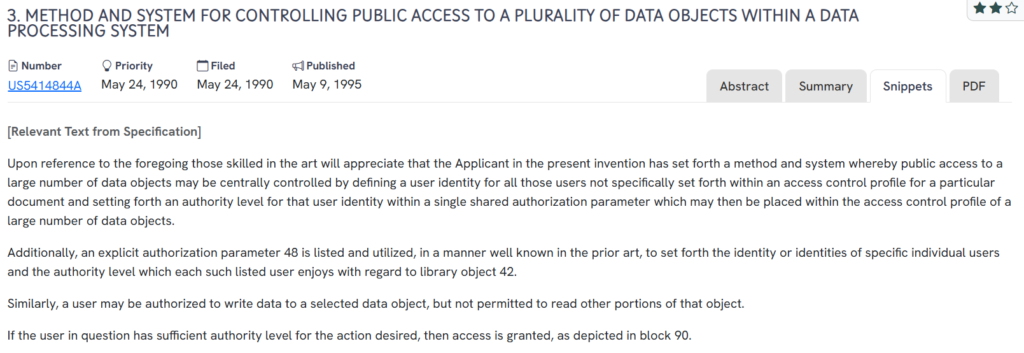
Source: GPS
What does this patent introduce to the landscape?
- Centralized access profiles: Shared authorization parameters can be applied to numerous data objects, streamlining permission management.
- Explicit user identity mapping: Specific users can be listed with defined authority levels for each document or data object.
- Granular action permissions: Users can be allowed to write data but restricted from reading certain content within the same object.
- Default identity handling: A public or generic user role is defined with baseline access for those not explicitly listed.
- Authority-level enforcement: Access decisions are made based on whether a user’s authority level meets the required threshold for an action.
How does it connect to US9465913B1?
While US9465913B1 focuses on securely storing personal information with tiered disclosure based on requester status, US5414844A introduces a scalable method for assigning access through shared profiles and specific user roles. Both systems emphasize layered authorization and precise control of what data each individual can access. They represent complementary strategies in regulating data access:
- Authority-based access enforcement using configurable thresholds
- Differentiated user roles for reading, writing, or modifying data
- Shared authorization profiles to simplify bulk permission assignment
Why does this matter?
US5414844A highlights an early and effective approach to centralizing access permissions for large datasets. It provides historical context to the evolution of permission-based controls, as seen in US9465913B1, highlighting how default access roles, user-specific rights, and action-based restrictions laid the groundwork for today’s secure data governance systems.
#5. JP2000267959A
This Japanese patent JP2000267959A, published in 2000, presents a network-based information sharing system where access to stored content is controlled through identification data and predefined user restrictions. The invention allows shared data to be accessed only by users who meet specific access criteria, including identification via company names or electronic certificates. It supports secure, multi-user environments where access rights are centrally validated and managed.
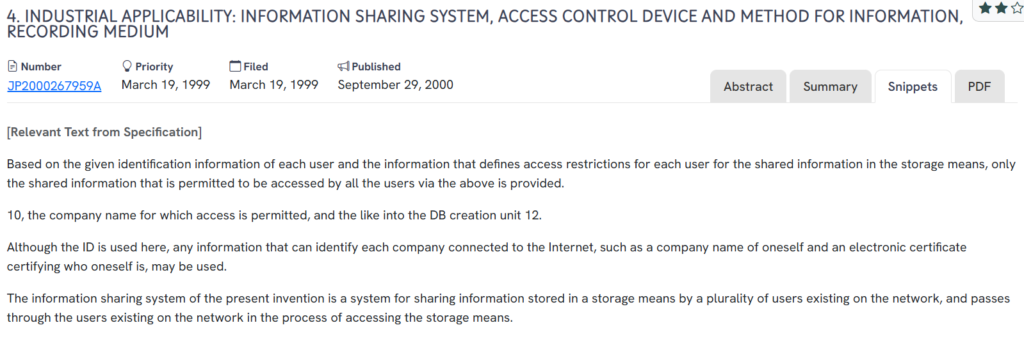
Source: GPS
What does this patent introduce to the landscape?
- User-specific access filtering: Only information explicitly permitted for a user, based on their ID, is accessible in the shared system.
- Company-level identity recognition: Entities are identified using company names or digital certificates to enforce access rules.
- Centralized restriction database: Access permissions are stored and maintained in a dedicated database tied to each user’s identification.
- Multi-user network access: The system supports concurrent access by multiple users across a network with permission checks at each request.
- Dynamic access delivery: Shared information is distributed in real time, based on identity validation and predefined sharing permissions.
How does it connect to US9465913B1?
While US9465913B1 controls access to personal data through role-based authorization, JP2000267959A manages shared content access using identification data and credential matching. Both systems ensure that only eligible users receive access to sensitive information, reinforcing selective visibility and access logging across distributed networks.
- Identity-based access control using user IDs or digital certificates
- Real-time filtering of data based on user-specific access rights
- Centralized management of permission rules across multiple users
Why does this matter?
JP2000267959A reinforces the importance of identity verification and centralized access control in shared digital environments. It parallels the access management goals of US9465913B1, showing how multi-user platforms can securely distribute data while preserving user-specific access rules. This patent reflects the broader trend toward identity-driven information sharing systems.
Related Read: Memory security often intersects with efficiency. US7057960B1 shows how segmented refresh reduces standby current, complementing US9465913B1 and similar patents’ focus on minimizing circuit exposure in secure arrays.
How to Find Related Patents Using Global Patent Search?
Understanding the broader innovation landscape around a patent like US9465913B1 is crucial for developing secure data systems, refining platform architecture, or benchmarking personal information frameworks. The Global Patent Search tool streamlines this process, providing an efficient path to discover inventions that share similar logic, structure, or access control mechanisms. Here’s how it works:
1. Enter the patent number into GPS: Start by entering the number, US9465913B1, into the GPS interface. The tool instantly transforms the input into a smart search, leveraging classification codes and keyword relevance to construct a comprehensive query.

2. Explore conceptual snippets: Instead of detailed claim mapping, GPS now returns intelligent text snippets. These highlight operational similarities across patents, pinpointing where access control, encryption logic, or identity-based authorization themes reappear.

3. Identify related inventions: The results reveal technologies that align with the system-level thinking of US9465913B1, such as secure digital repositories, permissioned data sharing, and networked identity verification models.
4. Compare concepts without legal framing: GPS removes the need to analyze legal claim language, instead focusing on structural and functional analogs that reveal how others have addressed similar challenges in data governance.
5. Accelerate cross-domain research: Whether you’re developing healthcare IT systems, user authorization platforms, or enterprise data layers, GPS supports quick navigation through a complex web of related patents and technologies.
With these capabilities, Global Patent Search empowers engineers, strategists, and system architects to decode the technological DNA of inventions like US9465913B1 and make smarter, faster research decisions across the patent landscape.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.