Some inventions are built for niche tasks. Others reshape our understanding of protecting digital content. US7203844B1 clearly belongs to the latter.
Patent US7203844B1 is mentioned in the case between Torus Ventures LLC and Healthmarkets Insurance Agency. This patent outlines a recursive security protocol designed to apply multiple layers of encryption to digital data, whether that data is software, media, or the tools used to access it. Importantly, this article does not explore the legal aspects of that case. Instead, we focus solely on the underlying technology and how it fits into a broader ecosystem of digital rights management.
Using the Global Patent Search (GPS) platform, we’ll highlight patents that mirror or extend the technical concepts found in US7203844B1. For technologists, IP analysts, and innovators in cybersecurity, this data-driven review reveals how encryption strategies continue to evolve.
Understanding Patent US7203844B1
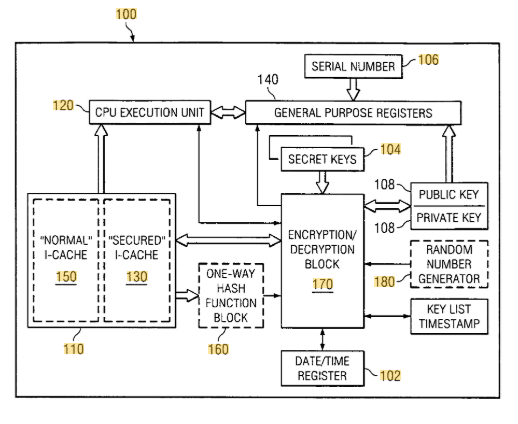
US7203844B1 describes a method and system for a recursive security protocol designed to protect digital content. It enables multiple layers of encryption on a digital bitstream, where each layer is associated with a corresponding decryption algorithm. This structure allows content to remain secure while supporting flexibility in key management and distribution.
Source: Google Patents
Its four key features are
#1. Layered encryption – A bitstream is encrypted using a first algorithm, then again with a second, forming a recursive security layer.
#2. Decryption pairing – Each encrypted layer is linked with a specific decryption algorithm for authorized access.
#3. Self-referencing protocol – The system is capable of securing not only digital media but also the security protocols themselves.
#4. Hardware or server-based key management – Decryption keys may reside in device hardware or be retrieved from secure servers.
The patent’s importance lies in its role in the broader context of digital rights management technologies. Its architectural design and recursive approach to encryption offer valuable insight into how content protection has advanced in distributed digital environments.
Similar Patents As US7203844B1
To map the technical ecosystem around US7203844B1, we ran it through the Global Patent Search tool. Below is a quick glimpse of the GPS tool in working:

Source: Global Patent Search
This surfaced several patents that explore comparable encryption frameworks, authentication mechanisms, and data control strategies. Below is an analysis of one such reference that highlights conceptual parallels in managing access and duplication of protected digital content.
Related: Explore how US9450956B1 leverages biometric-enabled proximity keys for automated authentication in secure environments.
#1. JPH07162410A
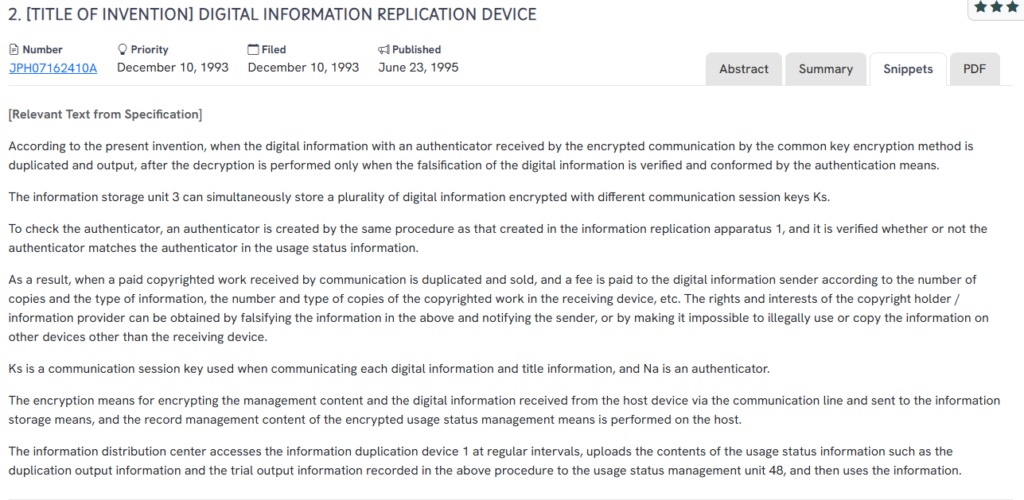
This Japanese patent, JPH07162410A, published in 1995, describes a digital information replication device that ensures secure duplication of encrypted content through authenticator validation and controlled decryption.
Source: GPS
What this patent introduces to the landscape?
Authentication-controlled duplication of encrypted content using session keys and remote verification.
- Authentication-driven decryption: Digital data is decrypted only if its integrity is verified through a matching authenticator.
- Session-specific encryption: Supports simultaneous storage of multiple encrypted bitstreams, each secured with a unique session key (Ks).
- Usage tracking and duplication control: Monitors the number and type of copies made and transmits this data to a central usage management system.
- Remote compliance enforcement: Regular uploads of usage logs enable centralized oversight and prevent unauthorized replication on other devices.
How it connects to US7203844B1?
- Both employ multi-layered encryption protocols tied to decryption logic.
- They share the use of key-based access controls that condition data usage on authentication.
- Each system supports the distributed management of encrypted digital assets.
- Remote or server-based tracking mechanisms ensure compliance with content protection rules.
Why this matters?
This reference highlights a foundational model for secure content duplication and usage reporting, ideas that directly parallel US7203844B1’s recursive encryption and self-validating protocol structure.
#2. JP2000098885A
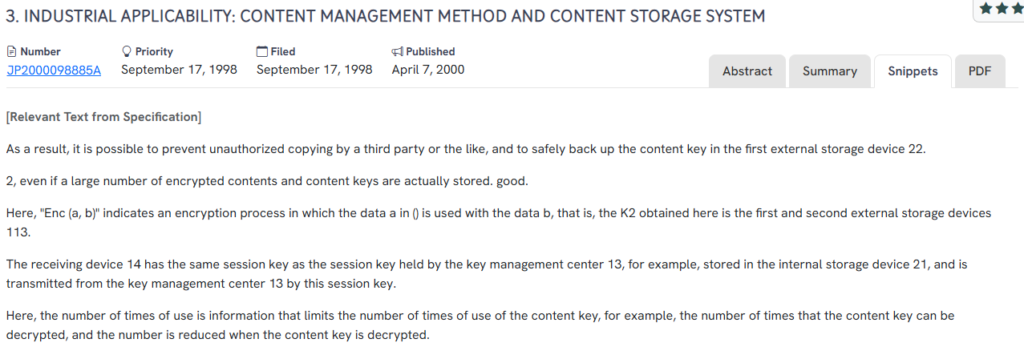
This Japanese patent, JP2000098885A, published in 2000, introduces a content management method and storage system that enforces encryption controls and usage limits for securely handling digital content keys.
Source: GPS
What this patent introduces to the landscape?
Encrypted content key management with usage restrictions and secure external storage.
- Session-key-based decryption: The receiving device decrypts content keys using a session key shared with a key management center.
- Controlled content key usage: Limits the number of times a content key can be used, decrementing with each decryption event.
- External secure storage: Backs up encrypted content keys in a trusted external device, reducing the risk of unauthorized copying.
- Multi-device content handling: Supports simultaneous encrypted content storage across multiple secure hardware environments.
Recommended Read: US9714133B2 – Spray tech patent Flairosol II combines piston systems and dome valves for sustainable, precision dispensing: a non-digital, mechanical engineering innovation.
How it connects to US7203844B1?
- Both patents rely on encrypted session keys for access control and content security.
- They use conditional decryption mechanisms that regulate content usage.
- The structure supports multi-tiered encryption and key verification, echoing US7203844B1’s recursive design.
- Secure key backup and limited-use licensing models align with the patent’s approach to controlled digital distribution.
Why this matters?
This reference contributes a critical model for usage-limited decryption and distributed content key management, principles central to the recursive and flexible protection system outlined in US7203844B1.
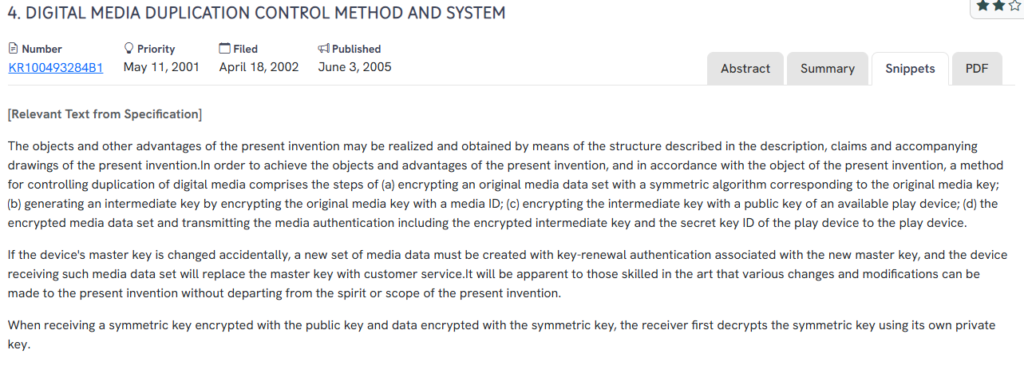
#3. KR100493284B1
This Korean patent, KR100493284B1, published in 2005, outlines a system for controlling digital media duplication using a multi-layer encryption process tied to device-specific authentication.
Source: GPS
What this patent introduces to the landscape?
Device-specific encryption and duplication control using public key infrastructure and layered keys.
- Layered encryption sequence: Media is first encrypted with a symmetric key, which is then encrypted with a media ID, and subsequently with the play device’s public key.
- Device-locked playback control: Only a registered playback device with the correct private key can decrypt the media, preventing unauthorized duplication.
- Key renewal mechanism: Allows regeneration of media data tied to a new master key if the original key is compromised or changed.
- Authentication-enabled delivery: Media authentication is tied to a specific device through a secret key ID, adding an extra verification layer.
How it connects to US7203844B1?
- Both patents utilize recursive or multi-step encryption processes to secure digital content.
- They enforce device-specific decryption, preventing playback or duplication on unauthorized systems.
- Each design incorporates public and private key infrastructures for authentication and controlled access.
- Key renewal and replacement mechanisms reflect US7203844B1’s focus on dynamic and adaptable security layers.
Why this matters?
This reference showcases how secure playback systems can integrate multi-layer encryption with device-specific validation, a foundational idea in US7203844B1’s recursive security protocol for managing and protecting digital content.
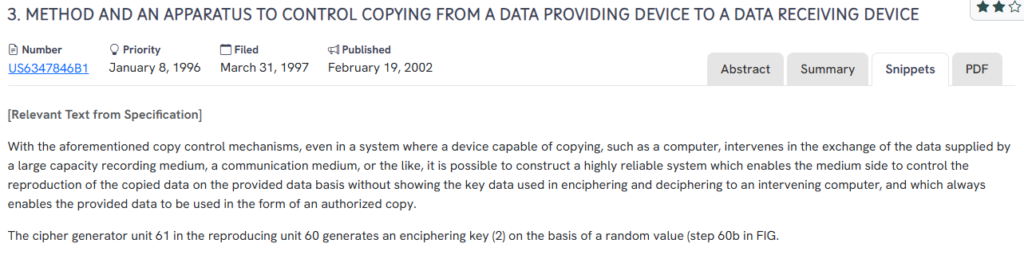
#4. US6347846B1
This U.S. patent, US6347846B1, published in 2002, introduces a method and apparatus for controlling data copying from a source to a receiver, enabling content use in authorized form without exposing decryption keys to intermediaries.
Source: GPS
What this patent introduces to the landscape?
Secure reproduction control using hidden key transfer and intermediate-proof encryption.
- Authorized copy generation: Allows copied data to be reproduced securely by ensuring the reproduction key is never exposed to intermediary systems.
- Enciphering key isolation: Encryption keys are generated and applied internally by the playback device, keeping sensitive keys hidden from external copying-capable devices.
- Randomized key creation: Uses random values to generate unique encryption keys, improving content protection robustness.
- Playback control at the media level: Ensures that only authorized devices can decrypt and reproduce the original content.
How it connects to US7203844B1?
- Both patents emphasize key confidentiality and secure transfer mechanisms.
- They prevent unauthorized decryption by binding playback rights to specific devices or pathways.
- Each framework uses internal key generation and randomized encryption logic.
- The focus on maintaining control at the content distribution level directly supports US7203844B1’s goals of recursive, layered security management.
Why this matters?
This patent reinforces the importance of hidden-key workflows and secure content reproduction, principles at the heart of US7203844B1’s architecture for multi-level encryption and controlled access.
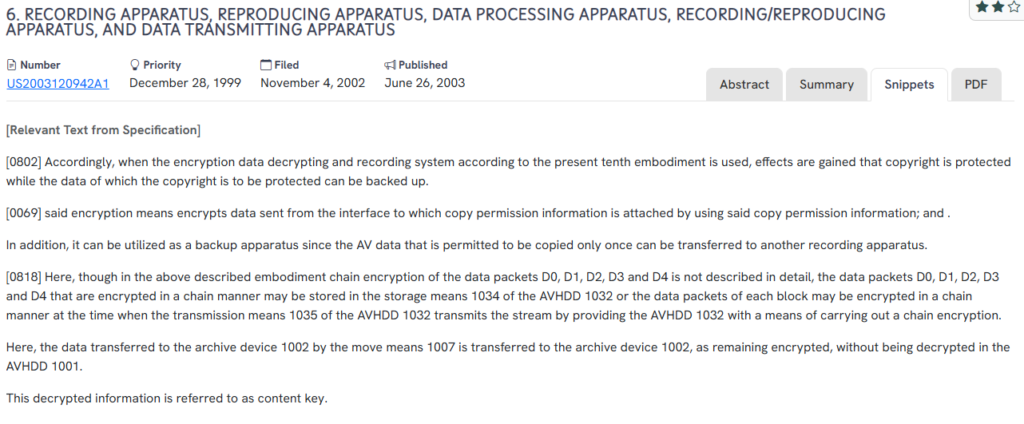
#5. US20030120942A1
This U.S. patent, US20030120942A1, published in 2003, presents a comprehensive recording and reproducing system that secures AV data using permission-based encryption and chain-encryption for stream transmission and backup.
Source: GPS
What this patent introduces to the landscape?
Permission-controlled encryption and backup for audio-visual data using chain encryption techniques.
- Permission-based encryption: Data is encrypted using copy permission information, ensuring that only authorized copies can be made.
- One-time copy enforcement: AV content designated for single-copy can be securely transferred to backup devices without violating rights.
- Chain encryption of data packets: AV streams can be encrypted block-by-block in a sequential (chained) manner during transmission or storage.
- Encrypted archival transfer: Backup data remains encrypted during transfer, ensuring secure storage without intermediate decryption.
How it connects to US7203844B1?
- Both systems apply multi-stage encryption protocols to control access and duplication.
- They implement authorization-driven encryption/decryption workflows for digital content.
- Chain encryption in US20030120942A1 parallels US7203844B1’s recursive encryption architecture.
- Both designs support secure data backup and reproduction, enforcing compliance through encryption mechanisms.
Why this matters?
This patent adds depth to the evolving approach of secure content management, emphasizing permission-aware encryption and backup- core elements echoed in the recursive and multi-layered encryption framework of US7203844B1.
How to Find Related Patents Using Global Patent Search?
Exploring related patents is essential for understanding how a technology fits into the broader innovation landscape. Whether you’re assessing competitive designs, evaluating technical novelty, or researching alternative solutions, the Global Patent Search tool offers a structured, efficient way to trace overlapping ideas and system architectures. Here’s how it works:
1. Enter the patent number into GPS: Start by entering a granted or published patent number. GPS automatically generates a refined natural language query, which users can customize to emphasize specific keywords or technical features.
2. Review snippet-based insights: Instead of basic keyword matching, GPS presents precise snippets drawn from similar patents. These highlight how comparable inventions address similar technical challenges or design goals.

3. Discover structurally related technologies: GPS identifies patents with aligned system-level logic, such as shared encryption models, authentication flows, or hardware-software integration strategies.
4. Compare architectures without legal complexity: The tool focuses on conceptual and technical alignment rather than claim interpretation, helping users spot functional similarities without legal jargon.
5. Expand cross-domain research: Whether working in data security, digital rights management, or content distribution systems, GPS streamlines the discovery of related innovations across industries and jurisdictions.
With these features, Global Patent Search enables deeper and faster analysis, helping innovators and analysts uncover meaningful connections in the evolving technology landscape.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.