Anyone who has managed digital systems knows how easily billing errors can happen. One small mismatch in data, and the numbers don’t add up.
That’s the problem Patent US8005457B2 set out to fix.
It introduces a system that cross-checks usage data between the user’s device and the network’s gateway. If the numbers don’t match, the session is stopped immediately, preventing billing errors and potential fraud.
Today, this same idea powers many cloud and telecom billing platforms and central to a litigation campaign. To see where this patent fits in the broader world of network billing verification, we used the Global Patent Search (GPS) tool to explore other inventions built on similar ideas.
Inside the Technology of US8005457B2
Think of every online session, i.e., streaming a movie, sending files, or joining a video call, as a small agreement between you and the network.
You use their bandwidth, and they charge you for it.
But what if the numbers that measure your use are wrong?
That’s the question Patent US8005457B2 tried to answer.
The inventors behind this patent built a system that never takes one side’s word for it. Both the user’s device and the network gateway keep their own records of how much data is used.
At regular intervals, the two records are compared. If they match, the session continues normally. If they don’t, the system immediately stops the connection before a wrong charge can go through.
It sounds straightforward, but that small loop of comparison changes everything. It turns billing into a live verification process instead of an afterthought.
It also creates a clear trail of data that cannot be altered or faked, because both ends are keeping score.
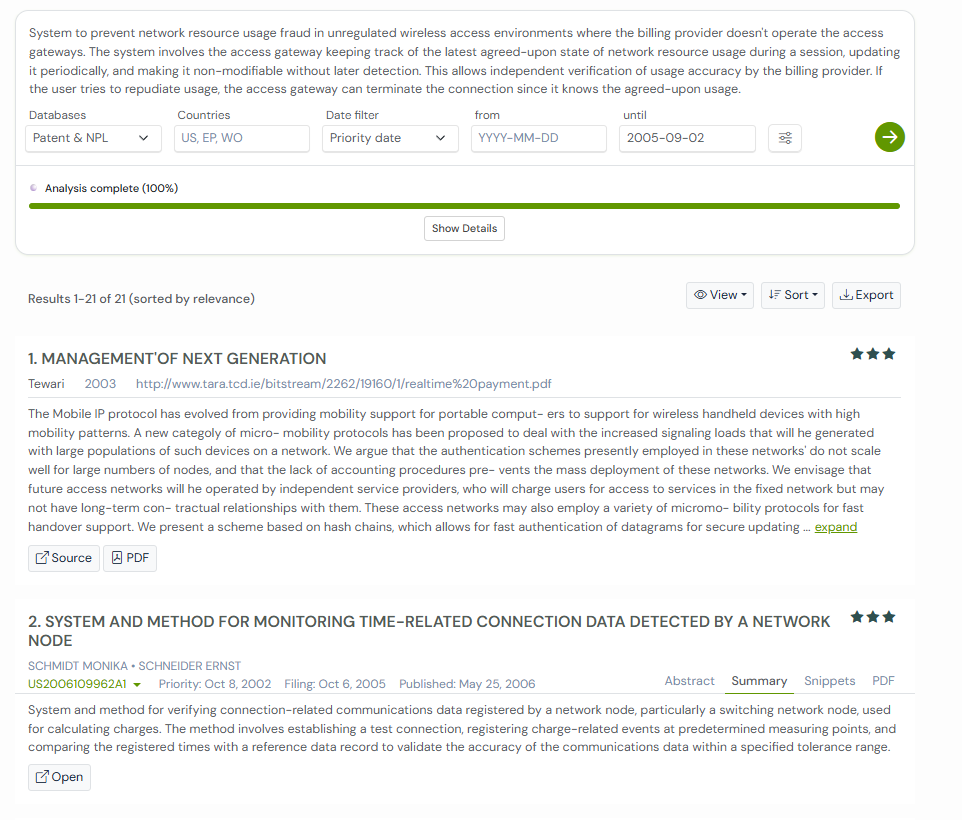
Key Features
The below features form the core of the patent’s novelty and make this system stand apart from earlier one-sided billing mechanisms.
- Two-way verification: Both the user’s device and the network gateway record usage data independently, then cross-check for accuracy.
- Encrypted records: Every data log is protected to prevent tampering or manipulation.
- Real-time tracking: The system monitors usage as it happens, not after the fact.
- Automatic session control: If a mismatch appears, the session ends immediately to stop errors or fraud.
Together, these ideas create a smarter, self-correcting billing model that balances trust between users and providers in real time.
Related Read: Network trust is also about how bandwidth is managed when every user competes for capacity. Explore our take on EP3107243B1 and 5 Patents That Make Wireless Networks Handle Congestion Better to see how device-assisted control policies preserve network efficiency through real-time, adaptive feedback.
Other Patents Working on the Same Idea
The story of US8005457B2 does not begin in isolation.
Years before it was filed, engineers across the telecom world were already asking a similar question: how do we make network billing more accurate and harder to manipulate?
One of the earliest answers came from Nokia Telecommunications.
1. AU8443398A – The Early Link Between Access and Billing
Filed in 1998, AU8443398A describes a system where billing is built directly into the process of connecting to a network.
Every time a user starts a session, the device sends a “start” message that triggers the billing clock.
When the session ends, the system generates a charging record, often verified through a digital signature to ensure authenticity.
It was an elegant first step toward billing that could keep itself in check.
The design made sure that every connection had a record, and every record could be verified, at least on one side. But this is also where its limits showed.
The system could measure time and data volume, but it relied only on the network’s record of what happened. There was no second opinion, no independent record from the user’s device.
That gap is exactly what US8005457B2 would later close, by adding the missing layer of cross-verification between the user and the gateway.
Why This Patent Matters
AU8443398A laid the groundwork for what came next.
It proved that billing could be integrated into access control. But it also revealed the need for something stronger: a two-sided check that could spot mismatches instantly.
That concept became the foundation for the smarter, self-verifying systems that followed, including US8005457B2.
For another look at how automated systems prevent revenue loss, our analysis of US8209267B2 shows how postal networks adjust tariffs in real time whenever a postage mismatch is detected.
2. US20020133613A1 – When Gateways Learned to Watch the Flow
Filed in 2001, US20020133613A1 marked the moment network gateways started doing more than just connecting users. They began watching everything that passed through them.
This invention introduced built-in analyzers and traffic meters that tracked internet data in real time. Every packet of information flowing through the gateway was measured, categorized, and tied to a user session.
It even linked directly to a billing system, so usage could translate automatically into charges.
But while it was great at tracking, it still trusted a single source.
The gateway collected the data, managed the speed, and decided the bill on its own. What it didn’t do was compare its numbers with the user’s device.
That missing second viewpoint became the breakthrough of US8005457B2. By adding cross-verification between both sides, it turned what this 2001 patent application started: monitoring into something smarter: mutual validation.
Related Read: Network efficiency doesn’t just depend on billing accuracy. It also hinges on how signals are discovered and measured. Explore EP3016464B1 and 5 Patents Shaping Signal Discovery in Mobile Networks to see how small cell systems evolved to optimize signal measurement and real-time coordination across dense telecom environments.
Why it Matters
This patent marked the shift from passive data counting to active billing control. It showed that visibility at the gateway could improve fairness and accuracy.
But without a matching record from the user’s end, the system still had blind spots. This is the exact weakness US8005457B2 later solved.
3. CA2376309A1 – When Billing Became Part of Access
Published in 2000 by Deutsche Telekom, CA2376309A1 approached billing from a different angle.
Instead of focusing on how much a user consumed, it focused on who was allowed to connect in the first place.
The patent described a telecom system where the act of logging in automatically triggered the billing process. If you were an authorized user, the network opened access and began charging within the same step.
In other words, it merged two systems that used to be separate: access control and billing.
This approach worked well for secure environments, where verifying identity mattered more than tracking data. But it didn’t measure how long a session lasted or how much data passed through.
Where CA2376309A1 made billing part of access control, US8005457B2 took the next logical step. That is turning billing into a data-driven verification loop that compared records between the user and the gateway.
Why it Matters
CA2376309A1 marked the point where billing stopped being an afterthought and became part of how a user connected.
It introduced the idea that billing should begin at the moment of access, but it lacked the measurement and verification layers that later became essential.
It showed who could connect; US8005457B2 figured out how much they actually used.
4. US6240091B1 – When Billing Became Truly Two-Sided
Published in 2001 by Nokia, US6240091B1 presented one of the most complete billing frameworks of its time.
It tackled a long-standing problem: how to make sure every charge recorded by the network matches what the user actually consumed. This patent introduced the idea of both ends generating and checking their own billing data.
The user’s terminal created a charging message based on its activity. At the same time, the billing system at the provider’s side generated another. Before a session ended, the two records were compared to confirm they aligned.
It also combined two metrics, time and data volume, so that billing could reflect not only how long a connection lasted but also how much information passed through.
That dual-metric approach made billing more transparent and fair. It reduced disputes caused by incomplete or inconsistent records. Where earlier systems trusted a single log, US6240091B1 built a conversation between devices.
That exchange, one record verifying another, is precisely what US8005457B2 later refined for modern digital and cloud networks.
Why it Matters
US6240091B1 was a turning point. It transformed billing from a one-way report into a synchronized verification process.
It set the foundation for real-time, fraud-resistant billing models. It also showed that reliability comes from two independent views of the same data, a concept that sits at the heart of US8005457B2.
5. CA2555767A1 – When Billing Moved to Wi-Fi Networks
Published in 2005 by Tatara Systems, CA2555767A1 brought network billing into the world of Wi-Fi.
It outlined a system where a subscriber gateway tracked how long each user stayed connected and how much data they used during that session. This information was then sent to the service provider’s billing system, which processed the charges.
In simple terms, it automated the way Wi-Fi networks handled billing data. The gateway became the link between users and the billing platform. That is, collecting, organizing, and forwarding session information without any manual input.
However, while the system handled tracking and data transfer effectively, it didn’t include a way to check the accuracy of the information. The gateway created one record and trusted it.
There was no second source or verification step to confirm that the data truly matched what the user consumed. That limitation set it apart from US8005457B2, which later introduced a cross-verification mechanism between the user’s device and the gateway to eliminate such gaps.
Why it Matters
CA2555767A1 reflected the next step in network billing, i.e., shifting from telecom to Wi-Fi environments. It proved that gateways could manage billing automatically, but it also revealed the need for two-way confirmation to ensure accuracy.
That verification step became the defining idea behind US8005457B2.
Comparison Summary: How Each Patent Compares with US8005457B2
| Patent | Filed / Published | Core Idea | Billing Approach | Verification / Data Check | Technical Overlap with US8005457B2 | Key Difference |
| US8005457B2 | 2004 / 2011 | Dual-sided system for verifying network usage data | Cross-checks billing info between user and gateway | Real-time, automatic mismatch detection | ||
| AU8443398A | 1998 (AU) | Early access-based billing system | Gateway initiates and records billing sessions | One-sided record, no cross-checking | Introduced link between network access and billing | No dual verification or real-time session stop |
| US20020133613A1 | 2001 (US) | Gateway monitors IP traffic and usage | Tracks bandwidth and activity at network edge | Partial – tracks usage but doesn’t compare records | Focus on usage metering and bandwidth control | Lacks two-record validation layer |
| CA2376309A1 | 2000 (CA) | Integrated access and billing authorization | Billing starts with login authorization | None – verifies identity, not usage | Conceptually ties access and billing control | Omits usage or data correlation mechanism |
| US6240091B1 | 2001 (US) | Dual billing messages in connectionless networks | Time- and data-based charging | Strong – both sides generate and verify records | Closest match – shares two-point verification model | Limited to specific network types, no session auto-stop |
| CA2555767A1 | 2005 (CA) | Wi-Fi gateway billing for service providers | Collects session length and data volume | Partial – sends record to provider without validation | Extends usage tracking to Wi-Fi environments | Missing cross-check between gateway and user device |
Tracing the Bigger Story with GPS Tool
Every invention exists inside a network of related ideas: designs, methods, and improvements that push the same problem forward.
The Global Patent Search (GPS) tool helps uncover that network. It brings together both patent filings and non-patent literature, showing how others have approached the same technical challenge from different angles.
Here’s how to make the most of the tool:
1. Start with your core invention: Enter the patent number, like US8005457B2, or describe the idea in plain English. For example “a system that verifies billing data between a user device and a network gateway.” GPS uses this as the anchor to find conceptually related work across patents and research papers.
2. Scan the relevant summaries: GPS surfaces short summary from within each result. These passages can come from claims or from the specification. They appear because they share common ground with your query, such as a similar mechanism, data flow, or verification step. Skim the summary first to understand what each work actually does without reading the full document.

3. Open the full document when it matters: If a summary looks close to your idea, check the snippets next, which have relevant text from the specification.
If it matches your intent, you can read the patent or NPL document for context. Note how the method is implemented, what signals or records are used, and whether the workflow matches your use case.
4. Explore across industries: Usage verification and session billing appear beyond telecom. You will see echoes in Wi-Fi networks, cloud metering, and IoT device accounting. You can go through the results to see how the same idea travels and changes from one domain to another.
GPS goes beyond keyword matching. It connects patents and research that share the same technical DNA, turning discovery into understanding.
For US8005457B2, that means seeing how billing verification began and how it continues to shape every digital network built on trust and accuracy.
Try the GPS tool today to explore these connections for yourself.
Frequently Asked Questions
1. Why were billing mismatches such a big issue in early digital networks?
In early telecom and internet systems, billing depended on single-point data, which was usually what the provider’s network recorded. If that data didn’t match what the user’s device actually consumed, it led to incorrect charges, customer disputes, and sometimes deliberate fraud charges.
2. Are similar billing verification systems still used today?
Yes, though they’ve evolved. The same cross-verifying concept now underpins how cloud services, Wi-Fi platforms, and IoT systems track consumption. Every time your cloud dashboard shows real-time usage or credit limits, you’re seeing a modern extension of this same verification logic.
3. Why is studying similar patents important for innovators and companies?
Because it helps you see how an idea matures. When you look at similar patents, you spot the small improvements that turned a basic concept into a dependable technology. For R&D teams, this context can prevent duplicate work, spark new designs, or reveal white spaces where innovation is still possible.
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search (GPS) tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.